- Use Protected Users group for Users Not services
- Members of the Protected Users group must be able to authenticate by using Kerberos ( NTLM is not supported which is what RDP fails back to ) with Advanced Encryption Standards (AES).
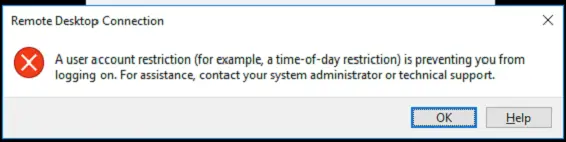
- Only the FQDN is supported to access via remote desktop because when you use IP adress, you will use NTLM for authentication. If you try you will see this
- Check if network flow ( Line of site ) is opened between client machine and domain controller RDPing for kerberos authentication
- Check SPN settings, if the server has many FQDN , you should add same SPNs for each FQDN
- Note that an unjoined domain client will absolutely do Kerberos. The username just needs to provide enough information to hint what domain they’re in. So instead of ‘admin’ use “[email protected]” and make sure the client has line of sight to the domain controller.
- For users outside the network without line of sight to the domain controller you can use KDC Proxy and proxy the RDP sessions through a gateway
- Failing that you can use an RMM service to access the server
- Do not disable CredSSP. Seriously. It’s the thing that guarantees you’re connecting to the right server, and protects the server from nosy clients.
