Recently had a customer be able to change passwords from Exchange webmail and for the password to sync back to their local computer without having direct access to the domain controller on a LAN or via VPN.
To trace this 365 support were able to use the below script from here
Download the file Auth.zip from https://cesdiagtools.blob.core.windows.net/windows/Auth.zip
Logs as shows :
To obtain the TGT we starting locating a DC and fail to find one standard Dclocator (expected as no VPN or connection to Domain Controller)
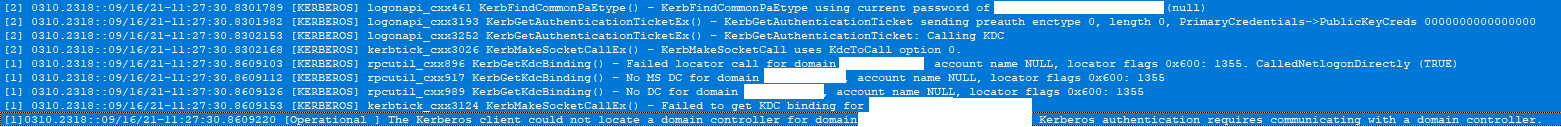
Now we see a call to KDCProxy, this is what is responsible for getting you authenticated without having a line of site to your DC.
Line two of this tells you the KDC proxy gateway is connecting too
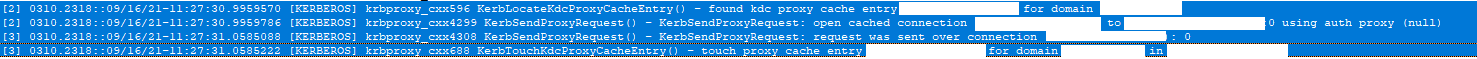
This is what we see when the correct password is entered.
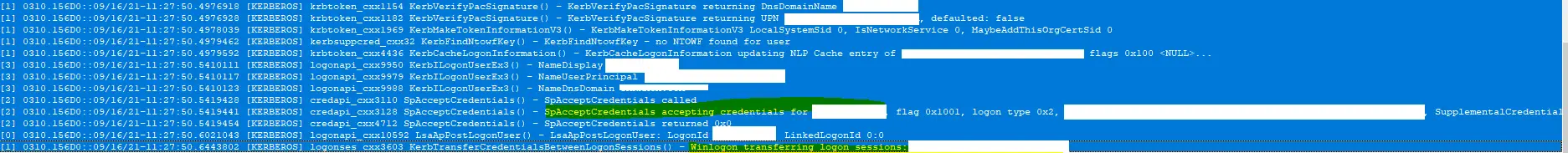
The question in my mind , was how was it able to get KDC proxy gateway address? Its a FQDB used by the RDP Gateway , and the below found my answer
“This is called the KDC Proxy Service (KPS), and it was introduced as a supporting service for Direct Access and Remote Desktop Gateway deployments”
KDC Proxy is installed with 2016 Server Remote Desktop Gateway role , so if you have a Terminal Server Enviroment listing on Port 443 which it needs for the Gateway you have this running!
But I have never seen this elsewhere and they have RDP Gateway roles?
This site gives a nice rundown of it all KDC Proxy for Remote Access (syfuhs.net) – There’s a little known feature in Windows called the KDC Proxy that lets clients communicate with KDC servers over an HTTPS channel instead of TCP.
By default , the Keys HttpsClientAuth and DisallowUnprotectedPasswordAuth do no exist in HKLM\SYSTEM\CurrentControlSet\Services\KPSSVC\Settings , however this setup they did
HttpsClientAuth : Dword 0 ( Disable client authentication )
DisallowUnprotectedPasswordAuth : Dword 0 ( Enable password authentication ) Which enabled this Password reset without connection to Domain Controller ( When DisallowUnprotectedPasswordAuth is set to 0 the KDC proxy will allow the user to retrieve a krbtgt using username and password. )
It must be secure to Enable this without Password Auth and Windows Hello instead as you open yourself up for a Brute Force attack ( as the Logins are not restricted and count towards lockout polices )
You need to make sure the user authenticating is using the primary domain name not an Alternate UPN
Failed to locate a domain controller in domain xxxxxxx.com.au with locator flags 0x601: error code 0x54B.