- Staff unable to connect to a new SSID.
- Authenticators report an ‘access-reject’ being returned from the NPS/RADIUS server.
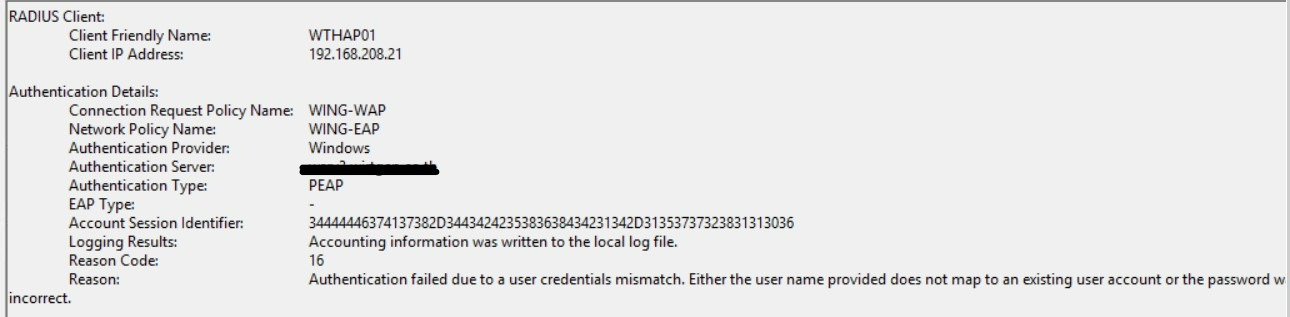
- NPS rejecting with reason code 16 (Bad username/password)
- You see NPS logs where you have an auth type of “PEAP” but the “EAP Type” is null / “-“
General background: dot1x/AD authentication for network connections can use either EAP or PEAP. EAP requires a valid certificate on the access point as well as on the NPS/RADIUS server. PEAP is transparent and you only need a valid certificate on the RADIUS/NPS server. By Valid – I mean trusted by the client; it does not need to explicitly be a public ca.
Cause:
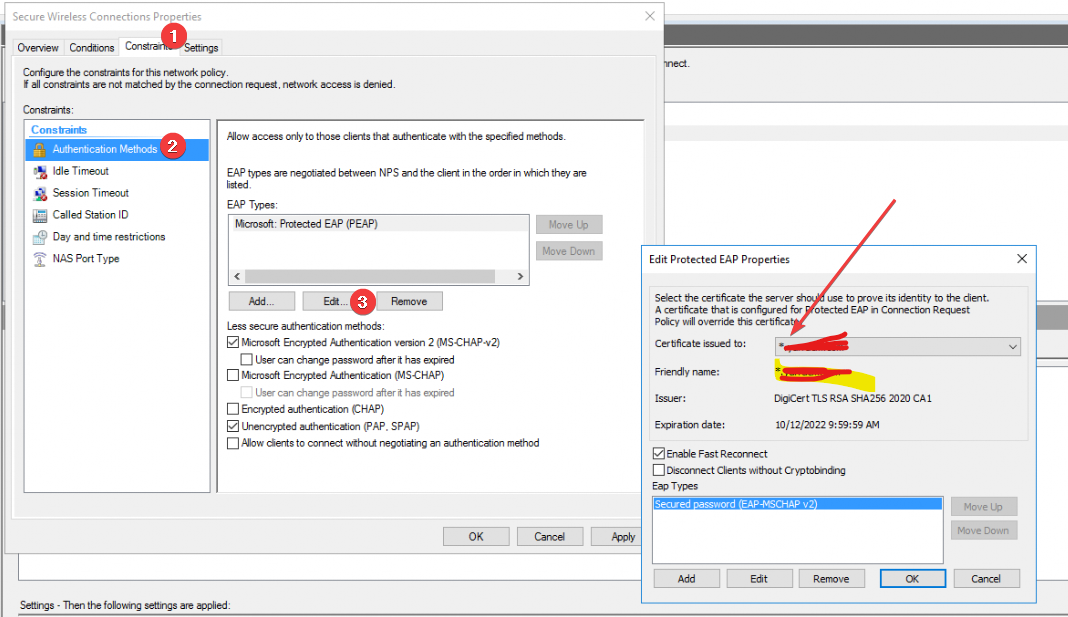
- NPS Server is configured to serve a certificate with a wildcard in the subject “*.yarracm.com” as an example.
- The original SSID has “do not validate ssl certificate”
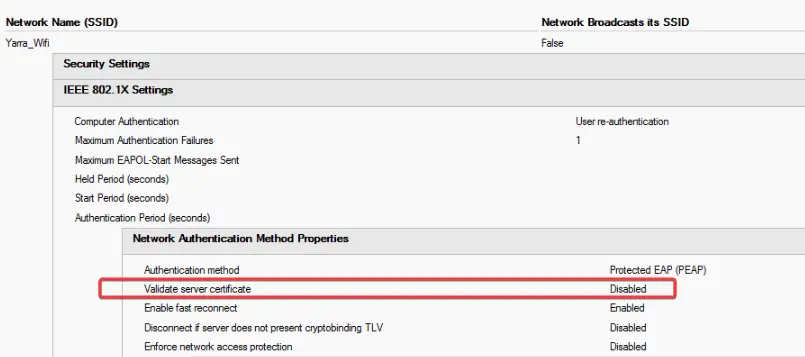
So in the new SSID the client is sent a certificate which has an invalid name, this invalid name. Because the certificate isn’t trusted it then doesn’t send the MSCHAPv2 credentials so you essentially are trying to login with a username but no password.
