Firstly, Spectre and Meltdown is a completely different class of flaws that is not the same as the traditional flaws. Hence, the industry is trying to quickly develop “workarounds” to mitigate them. And as we all know, workarounds and quick fixes has their impacts, and this is what we are seeing now with all the blogs about performance issues and confusion. This doesn’t mean we don’t do anything and ignore patching the flaw. We need to understand these flaws and patches, so the appropriate actions are taken.
As the industry work on better solutions, new better patches will be released and we need to know about them. Hopefully, the information below will help all of us to understand more about these vulnerabilities. Also, attached are the research papers released by Google Project Zero that started all these (if you are really interested).
Vulnerabilities summary and current mitigation approach
Spectre : CVE-2017-5753 : Variant 1 : Bounds Check Bypass
Compiler change; recompiled binaries now part of Windows Updates
Edge & IE11 hardened to prevent exploit from JavaScript
Silicon Microcode Update ALSO Required on Host : No
Spectre : CVE-2017-5715 : Variant 2 : Branch Target Injection
Calling new CPU instructions to eliminate branch speculation in risky situations
Silicon Microcode Update ALSO Required on Host : Yes
Meltdown : CVE-2017-5754 : Variant 3 : Rogue Data Cache Load
Isolate kernel and user mode page tables
Silicon Microcode Update ALSO Required on Host : No
The MS Patch Confusion
When the patch is applied to workstations the default behaviour is to enable the mitigations for both “branch target injection” and “rogue data cache load” vulnerabilities.
But when applied to servers, you have to enable these settings manually.
This can be verified by the powershell command provided by MS.
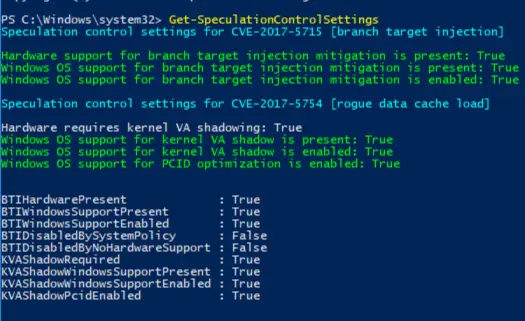
Performance Myth
On my Surface, when both mitigation are enabled, it slowed down my Surface significantly (feels like having HDD again, everything lags)
If you read the article in detail, you can actually override each mitigation individually or altogether.
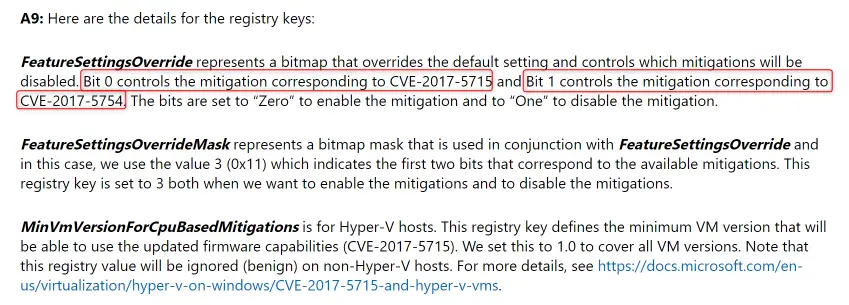
Setting FeatureSettingsOverride to 0x1, disable to mitigation for “branch target injection”, which is the one that (in theory) impacts on performance. After doing this, my Surface is back to normal again.
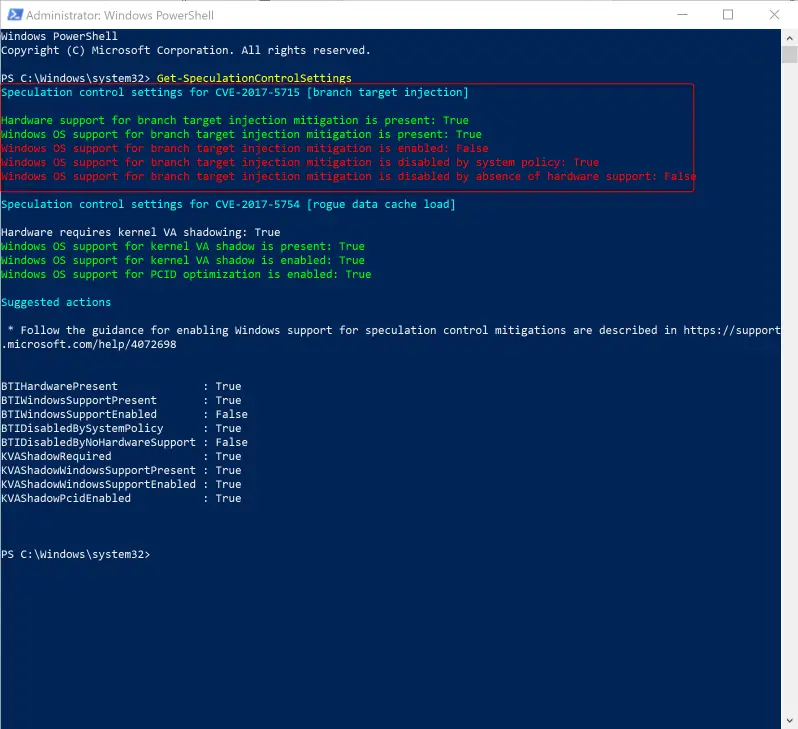
Take Away
- So if you don’t know about these registry keys and you have applied the patch to Windows servers 2008 R2 and 2012 R2, the mitigation is not in effect yet. Use the powreshell to verify that the mitigation is in place.
- Based on MS KB, performance impact applies to specific workload. Hence, do not blindly enable both mitigations on all systems. Suggestion is to,
- Enabled the mitigation for “rouge data cache load” first, this should have relatively lower performance impact comparing to the “branch target injection”.
- Once the above is done, go back and start applying the “branch target injection” patch one system at a time and observe performance impact. Revert, if performance degradation is too great.
Other Developments
- Google is claiming to have a mitigation for “Branch Target Injection” that doesn’t impact on performance. Intel apparently has admitted this is a better fix that what they have in development.
https://www.itnews.com.au/news/google-promises-spectre-fix-that-wont-slow-pcs-481132
