Recently had an issue where the RDweb Gateway was being brute forced locking out Accounts
The client did not want to hide the RDGateway behind the AppProxy due to issues with a shortcut not working 🙁
Unfortunately RDWeb Gateway proxy’s RDP Traffic over HTTP so normal WAF’s done work well with RDGateways ( WAFs usually have protection for Rate Limiting Connections )
But we can do this with IIS 🙂
Install this Role on IIS
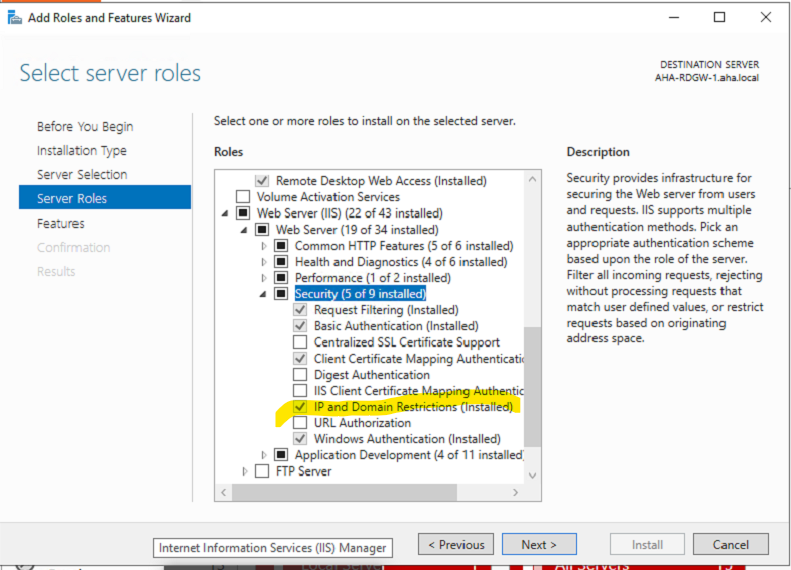
Enable Default Dynamics Restrictions on Logging Only Mode
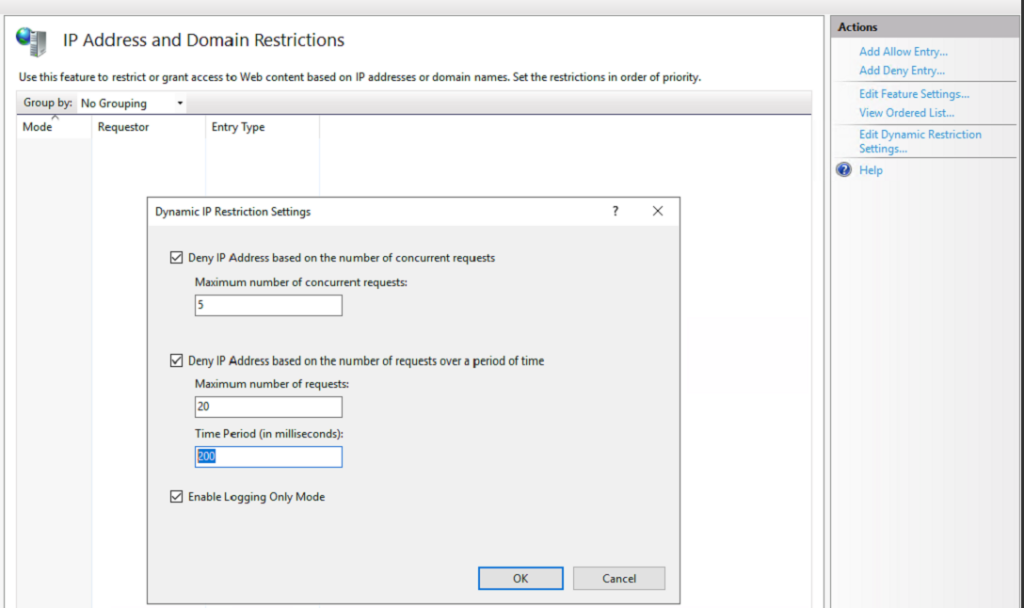
With enable logging only mode, request status as 200 and substatus code 501 or 502.
With enable logging only mode off , request status as 403 substatus code 501 or 502.
E.g. per below
#Fields: date time s-ip cs-method cs-uri-stem cs-uri-query s-port cs-username c-ip cs-version cs(User-Agent) cs(Referer) sc-status sc-substatus sc-win32-status time-taken
( log for normal dynamic restriction)
2018-01-08 04:30:34 192.168.2.50 GET / - 80 - 192.168.2.50 HTTP/1.1 Mozilla/4.0+(compatible;+MSIE+7.0;+Windows+NT+10.0;+WOW64;+Trident/8.0;+.NET4.0C;+.NET4.0E;+.NET+CLR+2.0.50727;+.NET+CLR+3.0.30729;+.NET+CLR+3.5.30729) - 403 501 0 15
( log entry for log only mode)
2018-01-08 05:37:11 192.168.2.50 GET /a.aspx - 80 - 192.168.2.50 HTTP/1.1 Mozilla/4.0+(compatible;+MLet make it easier for us to monitor this
Find and download Log Parser and Studio on webserver
How to emulate BruteForce
Open Chrome or Edge \ Developer tools , open network tab \ navigate to site , do a test login then copy the process login.aspx as fetch
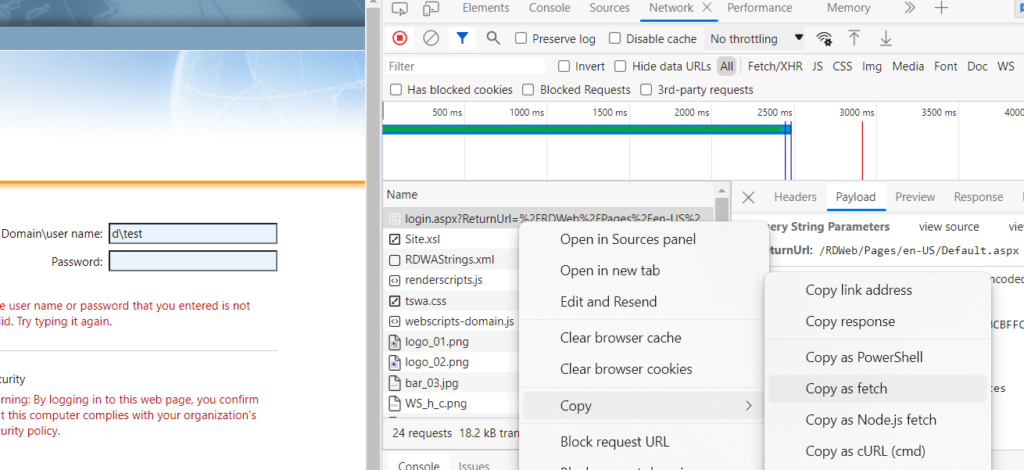
Paste it into the Console , press enter and keep repeating 10 times!
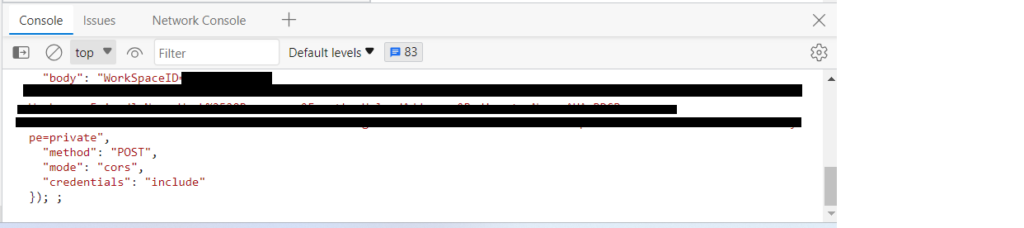
Go to Log Parser Studio
Import Logs
C:\inetpub\logs\LogFiles\W3SVC1
Create a new Query
SELECT c-ip,cs-uri-stem as Uri,
sc-status as HttpStatus,
sc-substatus as SubStatus,
sc-win32-status as Win32Status,
COUNT(*) AS Total
FROM '[LOGFILEPATH]'
WHERE (sc-substatus = 501) OR (sc-substatus = 502)
GROUP BY Uri, HttpStatus, SubStatus, Win32Status, c-ip
ORDER BY Total DESC
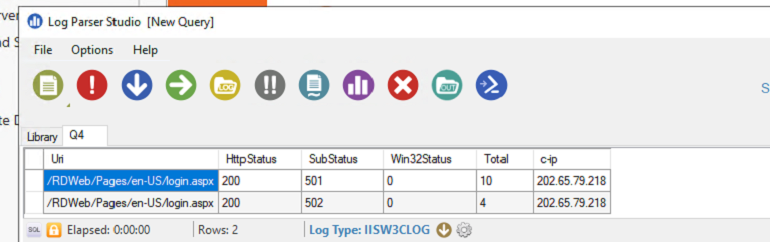
Then Execute ! We should see the blocks
Keep this on for a week then turn logged off for it to start blocking
You can see the IP List here for any blocks
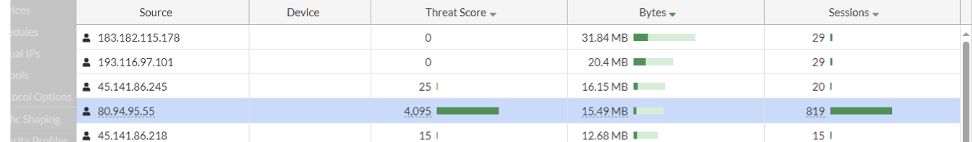
Doing this on Fortigate
1) Look at Geoblocking first of all as this will minimise the noise
2) Look at Session Limiting https://community.fortinet.com/t5/FortiGate/Technical-Tip-Limit-connections-to-a-specific-destination-IP/ta-p/244968
RDWeb.Brute.Force.Custom
Change SSL Inspection certificate to > deep-inspection
2.1 Enable the “Decrypted Traffic Mirror” > Create the profile for “New Decrypted Traffic Mirror”
2.2 Name : whatever name
2.3 Destination MAC: leave it default
2.4 Decrypted Traffic Type: Both
2.5 Decrypted Traffic Source: Both
2.6 Interface: select one interface never use before
use it and Apply on the Policy.
Go to Network > Diagnostics > select the interface we configure from the “New Decrypted Traffic Mirror”
4.1 Enable Filter > Host enter your testing IP/Internet IP
4.2 Start capture > all process have to start at testing machine begin open browser, enter wrong password and close the browser session.
4.3 Save the file and send to the Fortinet IPS team.
4.4 change the SSL inspection certificate for your original one.
This is the whole process what I did for the capture packet on the Fortinet.
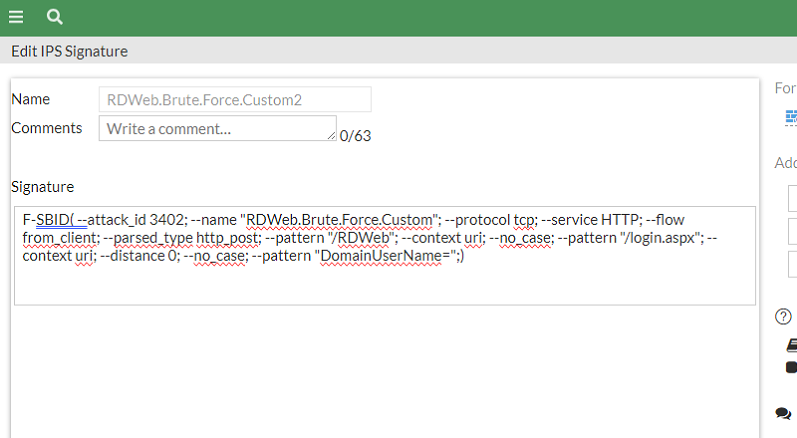
IPS Signature
F-SBID( --attack_id 3402; --name "RDWeb.Brute.Force.Custom"; --protocol tcp; --service HTTP; --flow from_client; --parsed_type http_post; --pattern "/RDWeb"; --context uri; --no_case; --pattern "/login.aspx"; --context uri; --distance 0; --no_case; --pattern "DomainUserName=";)
If you want to capture this IPS/IDS logs for the RDS https brute force attack, you also have to enable the “deep inspection” and Enable the “Decrypted Traffic Mirror”.
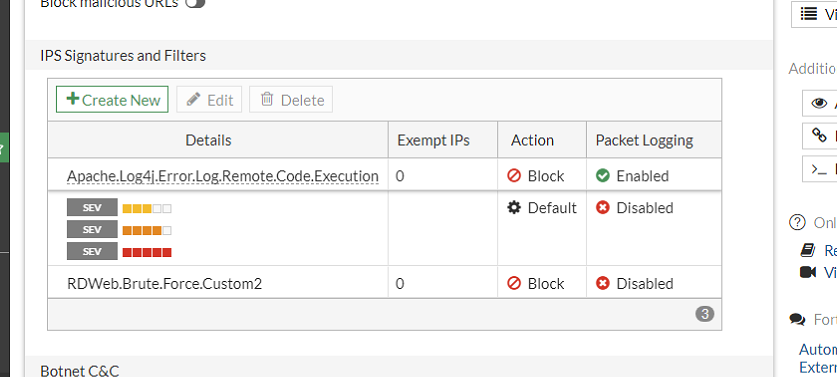
An addition to the great recommendations in this post, you can also leverage the “rate based signatures” section in the IPS Sensor. FortiGate has a signature specific for Microsoft Remote Desktop specifically (MS.RDP.Connection.Brute.Force).
