Per information :https://www.4armed.com/blog/llmnr-nbtns-poisoning-using-responder/ , in a Pentest you might fail this unless you do the below
- Disabling LLMNR:
- Open the Group Policy Editor in your version of Windows
- Navigate to Local Computer Policy > Computer Configuration > Administrative Templates > Network > DNS Client
- Under DNS Client, make sure that “Turn OFF Multicast Name Resolution” is set to Enabled
- Also V important do the Registry Change Here: mDNS – The informal informer | f20
- Intune :
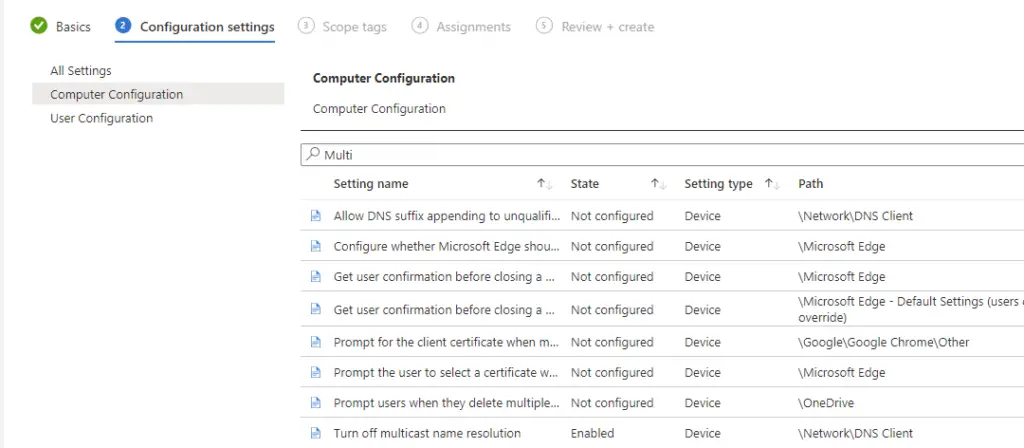
- Netbios over TCPIP disabled
- DHCP option “001 Microsoft Disable Netbios Option” configured for all scopes with value of 0x2
- NetbiosOptions value changed to 2 in registry for all interfaces with PS script
- LLMNR disabled using GPO
- Configured Secure only dynamic updates for all DNS zones
- WPAD
- Microsoft suggested workaround applied, powershell script to add to host file (https://docs.microsoft.com/en-us/security-updates/SecurityBulletins/2016/ms16-077)
- Added option 252 on DHCP scopes and pointed WPAD to 255.255.255.255
- REG ADD “HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Wpad” /v “WpadOverride” /t REG_DWORD /d “1” /f
