We use Radius and NPS for Authentication , we had the below Defender for Identity show up
Prevent users to request a certificate valid for arbitrary users based on the certificate template (ESC1)
Resolutions were :
Identify the vulnerable certificate template. Perform at least one of the following possible remediations:
1. Disable the “Supply in the request” configuration.
2. Remove EKU’s enabling user authentication (e.g Client Authentication).
3.Remove overly permissive enrollment permissions, which allows any user to enroll certificate based on that certificate template.
4.Enable “CA certificate manager approval” requirement.
We changed the below
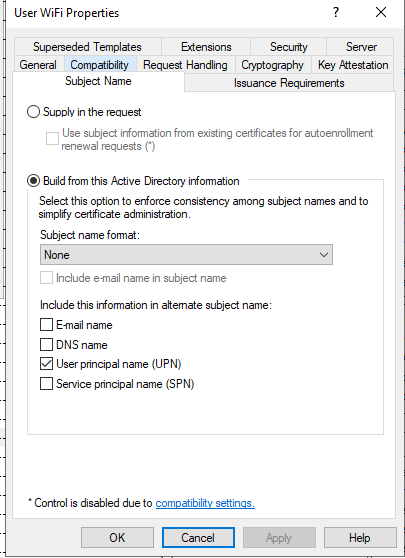
2) We can’t do this needed for Wifi Auth
3) Can’t do this Users need to enroll
4) Can’t do this don’t want manual approval
