Recently a customer Mimecast configuration let an email through marked as
High Risk Cred Phishing
Turns out their Spam Detection Action was set to Tag Headers instead of Hold for Review!

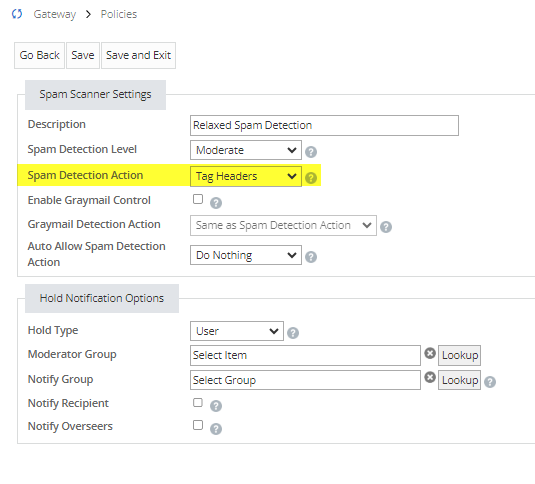
Mimecast Spam Scanning uses a combination of proprietary technology in conjunction with third party technology partners in order to provide a layered spam scanning approach. While our engines are taking updates from our technology partners 24 hours a day, we also write our own spam signatures in house. Signatures written for our “spam” engine are often built to detect phishing and malware — much more than just spam.
Mimecast looks at the body, formatting, source, header and any URIs in the body when scanning an email. Based on patterns, or combinations of patterns, a spam score is applied. There are tens of thousands of patterns. For instance, things like sending to undisclosed recipients, using SMTP Authentication, URL Shorteners, or SPF/DKIM/DMARC failures can add points to the spam score. However, none of them would be enough for a hold on their own. When patterns like this are found in conjunction with other spam characteristics, the score increases. Based on the findings or a combination of elements Mimecast will make a decision and based on that an email is allowed through, held or rejected. Our spam engine works by giving each email a spam score.
Relaxed 7-27 = hold
Moderate 5-27 = hold
Aggressive 3-27 = hold
Emails would need to be scanned for them to be blocked. Emails scoring 28 or higher are always rejected
The only way to block the emails would be to change the spam scanning configuration. It is best practice to have your Spam Detection Action set to “Hold for Review”
