Anti-Spoofing
*Are these policies working for the organization?
Please look toward the following link for better insight on the policy:
https://community.mimecast.com/s/article/email-security-cloud-gateway-configuring-anti-spoofing
Auto Allow
Please consider the following for a better security posture:
- Auto allow policy set to ” Apply auto allow strict” this will enforce a 1 to 1 relationship in case of any third party outbreaks.
2.Set the addresses based on to “Both”
Please look toward the following link for better insight on the policy:
https://community.mimecast.com/s/article/email-security-cloud-gateway-configuring-auto-allow-policies
Permitted Senders
*Consider adding some entries to the profile group.
Please look toward the following link for better insight on the policy:https://community.mimecast.com/s/article/email-security-gateway-permitted-senders-policy-configuration
Spam Scanning
*Auto allow actions should be set on the definitions.
*Questions around the multiple policies.
Please look toward the following link for better insight on the policy:https://community.mimecast.com/s/article/email-security-cloud-gateway-spam-scanning-policy-configurations
Attachment Protection
Additionally please note that the UI in the definition of attachment protection has changed please look toward the following links for further insights:
Impersonation Protection
*Consider creating a VIP policy instead of having multiple policies.
Please note that if you find that your VIP personal are being attacked or impersonated often please look to making a VIP policy where it is set to one hit with the customer display names enabled and filled in accordingly please look toward the following link for better insight.
https://community.mimecast.com/s/article/email-security-cloud-gateway-impersonation-protection-guide
URL Protection
*Configured correctly.
Please look toward the following link for better insight on the policy:https://community.mimecast.com/s/article/email-security-cloud-gateway-configuring-url-protection
Internal Email Protection
Setup
- Remove text on stationary ( HTML and plain text ) before sending emails via Mimecast
- Disable Office 365 Spam Filter
Maintenance
- Enabled Digest Sets every Hour ( not every 4 hour )
- Disable Device Enrollment
- Log on to the Administration Console.
- Click on the Administration menu item.
- Select the Account | Account Settings menu item.
- Expand the User Access and Permissions section.
- Select the Targeted Threat Protection Authentication option.
- SAML for Authentication SSO via a provider like Office 365 for 2fa and Brute Force protection. If not Fall back to LDAPS ( EWS basic Auth is not Secure )
- Disable Cloud Auth ( Or enable only for Continuity , and expire logins after 30 days )
- Service Monitoring Setup
- Acknowledge Disabled Users ( Make sure Receipt Validation is set to Known
- Setup impersonation protection for VIP
- Restrict Administration Console to IP
- Continuity Test
- Confirm you have an account as Super Admin
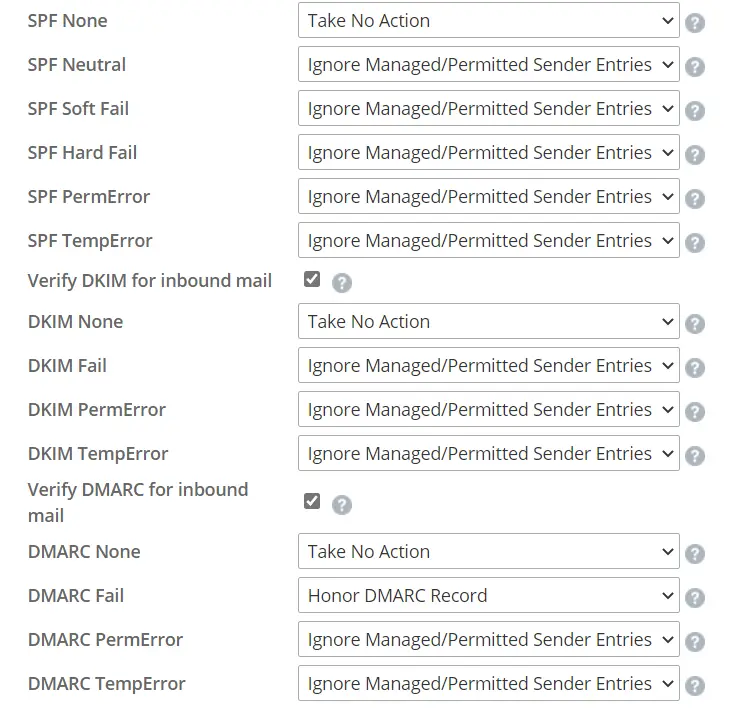
- Enable Outbond DKIM\SPF\DMARC
- Inbound ( this we recommend a “Reject” setting. Out of the box we set it to ignore/managed permitted sender entries as some customers didn’t like that it was too aggressive. )