AzureDiagnostics
| where ResourceType == "APPLICATIONGATEWAYS" and OperationName == "ApplicationGatewayFirewall" and action_s == "Blocked"AzureDiagnostics
| where ResourceType == "APPLICATIONGATEWAYS" and OperationName == "ApplicationGatewayFirewall" and action_s == "Blocked"
| summarize AggregatedValue = count() by requestUri_s, _ResourceId
| sort by AggregatedValue descAzureDiagnostics | where ResourceProvider == "MICROSOFT.NETWORK" and Category == "ApplicationGatewayFirewallLog" and action_s == "Blocked"| summarize count() by ruleId_s, bin(TimeGenerated, 1m),requestUri_s | sort by TimeGenerated desc
How to Track HTTP Status 504
AzureDiagnostics
| where OperationName == 'ApplicationGatewayAccess'
| where httpStatus_d == 504
| summarize count() by bin(TimeGenerated,1h)
| render columnchartTrack Azure WAF 949110
You need to use the TransactionID_g of a blocked Result which will then give you what leads up to the “inbound anomaly score exceeded azure Waf”
AzureDiagnostics
| where ResourceType == "APPLICATIONGATEWAYS" and OperationName == "ApplicationGatewayFirewall" and transactionId_g == "4cdf74f3-04bb-585c-9059-2110c8dc486a"
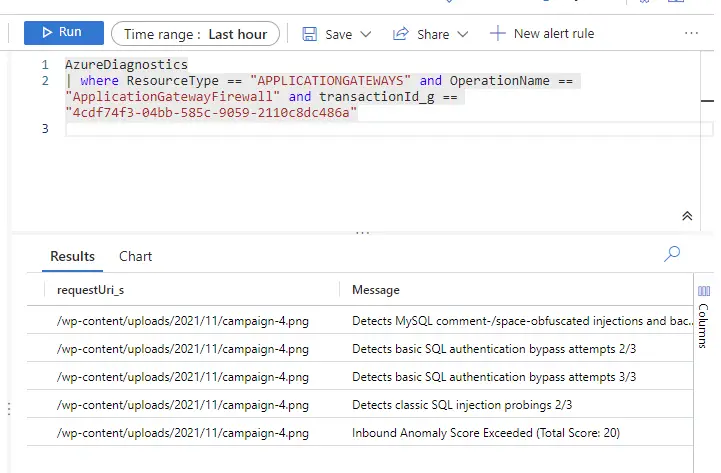
942200 REQUEST-942-APPLICATION-ATTACK-SQLI
942340 REQUEST-942-APPLICATION-ATTACK-SQLI
942370 REQUEST-942-APPLICATION-ATTACK-SQLI
949110
Check the Details_data_s
{“:”AUVIC”,”r found within [REQUEST_COOKIES:_tracking_consent:%7B%22region%22%3A%22AUVIC%22%2C%22reg%22%3A%22%22%2C%22con%22%3A%7B%22CMP%22%3A%7B%22m%22%3A%22%22%2C%22a%22%3A%22%22%2C%22p%22%3A%22%22%2C%22s%22%3A%22%22%7D%7D%2C%22lim%22%3A%5B%22CMP%22%5D%2C%22v%22%3A%222.1%22%7D]}
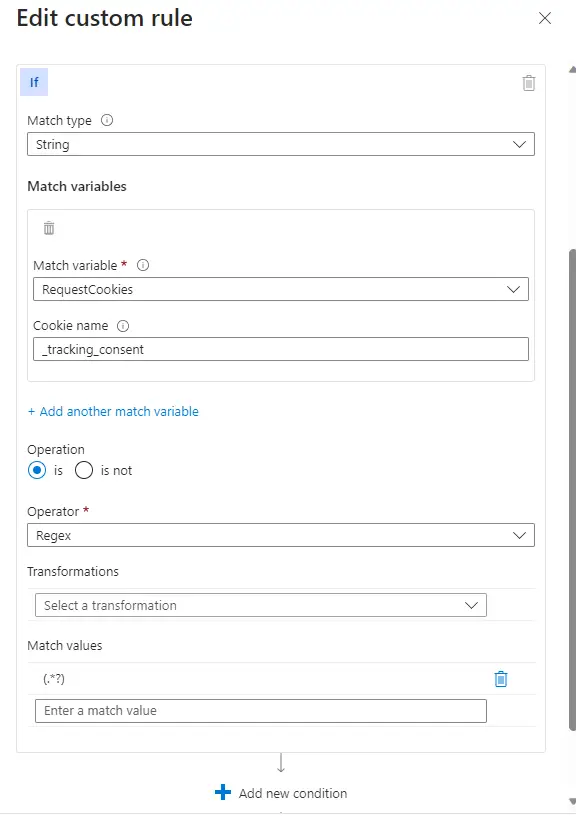
This _tracking_consent is a shopify Cookie!
Ok we can whitelist it via Custom Rule
AzureDiagnostics
| where ResourceType == "APPLICATIONGATEWAYS"
| where OperationName == "ApplicationGatewayAccess"
| where httpStatus_d == 403
| project TimeGenerated, Resource, clientIp_s, requestUri_s, transactionId_g, httpStatus_d
| join kind=leftouter (
AzureDiagnostics
| where ResourceType == "APPLICATIONGATEWAYS"
| where OperationName == "ApplicationGatewayFirewall"
| project transactionId_g, action_s, ruleId_s, ruleGroup_s, Message, details_message_s, details_data_s, details_file_s
) on transactionId_g
| extend
MatchedData = details_data_s,
RuleDetails = strcat(
"RuleID: ", ruleId_s,
" | Group: ", ruleGroup_s,
" | Action: ", action_s,
" | Message: ", Message,
" | Location: ", details_file_s,
" | Matched: ", details_data_s
)
| project
TimeGenerated,
Resource,
clientIp_s,
requestUri_s,
transactionId_g,
httpStatus_d,
action_s,
MatchedData,
RuleDetails
| order by TimeGenerated desc