2020 LDAP channel binding and LDAP signing requirements for Windows (KB4520412)
https://evotec.xyz/four-commands-to-help-you-track-down-insecure-ldap-bindings-before-march-2020/
https://www.petenetlive.com/kb/article/0001645
If the LdapEnforceChannelBinding key is not present, the server will use the new default value of 2 (enforced) after the patch with the LDAP changes is applied (rescheduled to 2nd half of 2020 – NOT in March 2020).
If you set it manually to 0, 1 or 2 the patch will have no effect, since windows will always respect this manual setting.
Important The March 10, 2020 updates do not change LDAP signing or LDAP channel binding default policies or their registry equivalent on new or existing Active Directory domain controllers.
Enable Logging
Reg Add HKLM\SYSTEM\CurrentControlSet\Services\NTDS\Diagnostics /v “16 LDAP Interface Events” /t REG_DWORD /d 2
LDAP Signing Events
Let’s start with LDAP Signing event logs. Remember that these logs exist since Windows Server 2008, and available regardless of the March 10 Windows Update.
| Event ID | General Description | Trigger | Required Logging Level |
| 2886 | A summary event-triggered once every 24 hours and indicating that this domain controller is not aligned with Microsoft’s best practices and can be significantly improved by configuring the server to enforce validation of LDAP signing. | Triggered every 24 hours, on startup or start of service if the Group Policy (Domain controller: LDAP server signing requirements) is set to None. | 0 or higher |
| 2887 | A summary event-triggered once every 24 hours and indicating how many LDAP binds that do not request signing and LDAP simple binds that are performed on cleartext have occurred. | Triggered every 24 hours when Group Policy (Domain controller: LDAP server signing requirements) is set to None and at least one unprotected bind was completed. | 0 or higher |
| 2888 | A summary event-triggered once every 24 hours and indicating how many LDAP binds that do not request signing and LDAP simple binds that are performed on cleartext have occurred (and rejected due to the “Require Signing” option). | Triggered every 24 hours when the Group Policy (Domain controller: LDAP server signing requirements) is set to Require Signing and at least one unprotected bind was rejected. | 0 or higher |
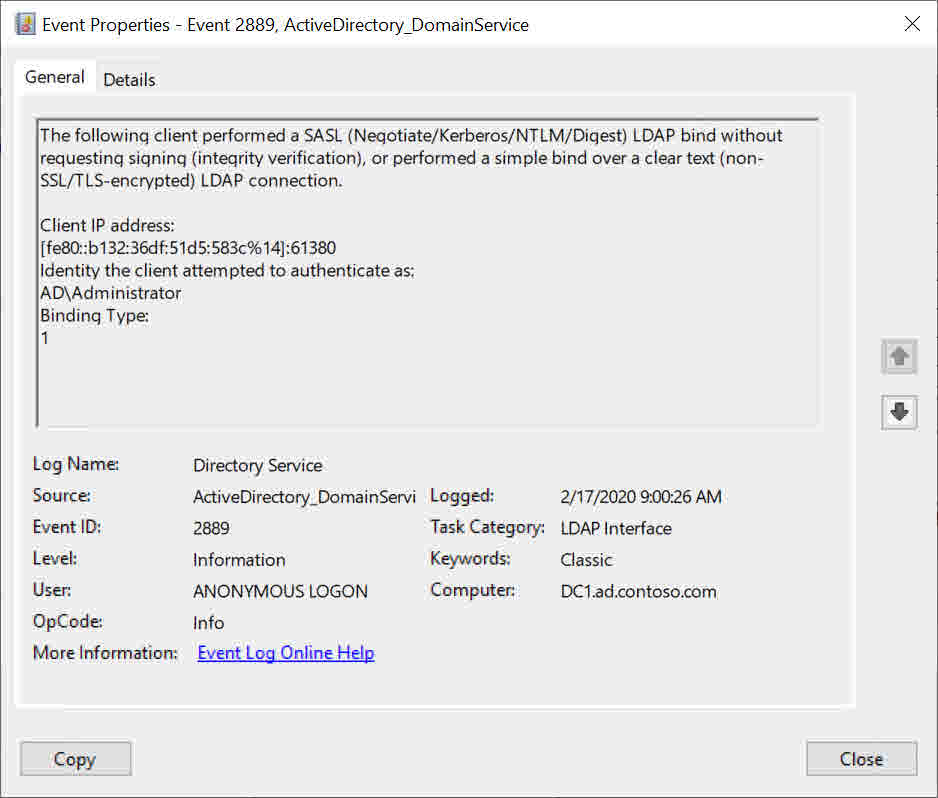
| 2889 | An event triggered every time a client performs LDAP binds that do not request signing or LDAP simple binds using cleartext. The event includes the client IP address and the authentication context (like authenticated user). | Triggered every time a client does not use signing for binds on sessions on port 389. | 2 or higher |
You can use Registry
Reg Add HKLM\SYSTEM\CurrentControlSet\Services\NTDS\Parameters /v “LdapEnforceChannelBinding” /t REG_DWORD /d 2
Also if you download the latest SCT 1.0 (security compliance toolkit) https://www.microsoft.com/en-us/download/details.aspx?id=55319 you will find template “SecGuide.admx” and language file “SecGuide.adml” that you can import in your policies (Central Store or C:\Windows\PolicyDefinitions) and from which you can manage Extended Protection for LDAP…..(CBT)
Consider modifying Group Policy setting “Domain controller: LDAP server channel binding token requirements” as “When Supported”. Remember to check that CVE-2017-8563 is installed on any supported OS.
Configuring the clients
How to enable LDAP signing – Windows Server | Microsoft Learn
Using a new group policy, first change the settings Network security: LDAP client signing requirements.
This can be found under: Computer Configuration > Policies > Windows Settings > Security Settings > Local Policies > Security Options.
Group policy to prepare clients for LDAP signing
The option is set to Negotiate signing. Wait until the setting has been applied to all clients.
Adjusting the domain controller
As soon as the change has affected all clients, create another group policy. In the same path as in the previous step, modify the setting Domain controller: LDAP server signing requirements.
Enforce signing of the LDAP communication for the domain controller
There, select the Require signing option. Then, link the GPO to the domain controller container.
Finalizing the clients
If the changes are now also active on the DCs, the group policy from the first step can be adapted so that the clients also require LDAP signing.
The option Network security: LDAP client signing requirements can now simply be changed from Negotiate signing to Require signing.
Activating channel binding
Channel binding is configured on the domain controllers by adding or modifying a corresponding entry in the registry. If it does not already exist, create a new DWORD entry under HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\NTDS\Parameters with the description LdapEnforceChannelBinding. The values to be assigned are as follows:
DWORD-Value 0: Disabled
DWORD-Value 1: Enabled, if supported
DWORD-Value 2: Always enabled
In the long term, a value of 2 is recommended, but for the transition phase, the option with a value of 1 can be a good compromise. After the change, the respective domain controller must be restarted.
Since the March 2020 update, the group policy Domain controller: LDAP server channel binding token requirements has been available for this purpose. There, you can choose between the options Never, When supported, and Always.
Configuring channel binding for domain controllers via GPO
Before January 2020 Update:
– Install all required Updates
– All DCs: Reg Add HKLM\SYSTEM\CurrentControlSet\Services\NTDS\Diagnostics /v “16 LDAP Interface Events” /t REG_DWORD /d 2
– All DCs: Monitor 2887 and 2889 Events
– All DCs: LDAP Channel Binding = 1 (Before Jan 2020 updates this setting is 0)
– Group Policy (Domain Level): Network security: LDAP client signing requirements: None (Before Jan 2020 updates this setting is Negotiate Signing)
– Group Policy (Domaincontrollers): Domain controller: LDAP server signing requirements: NoneAfter January 2020 Update:
– Domain controller: LDAP server signing requirements: Require (from Update)
– All DCs: LDAP Channel Binding = 1 (from Update)
– All DCs: Monitor 2888 EventsIf Problems:
– Domain controller: LDAP server signing requirements: None
– All DCs: Monitor 2887 and 2889 EventsIf all should be good:
– Network security: LDAP client signing requirements: Require
– Domain controller: LDAP server signing requirements: Require
– LDAP Channel Binding = 2
