Customer has 2012 DC’s with NPS and the Azure MFA extension for their Cisco Meraki Client VPN
All staff were not able to connect to the VPN from 8am. I have not found why it started at this time. Users before this were able to log in…
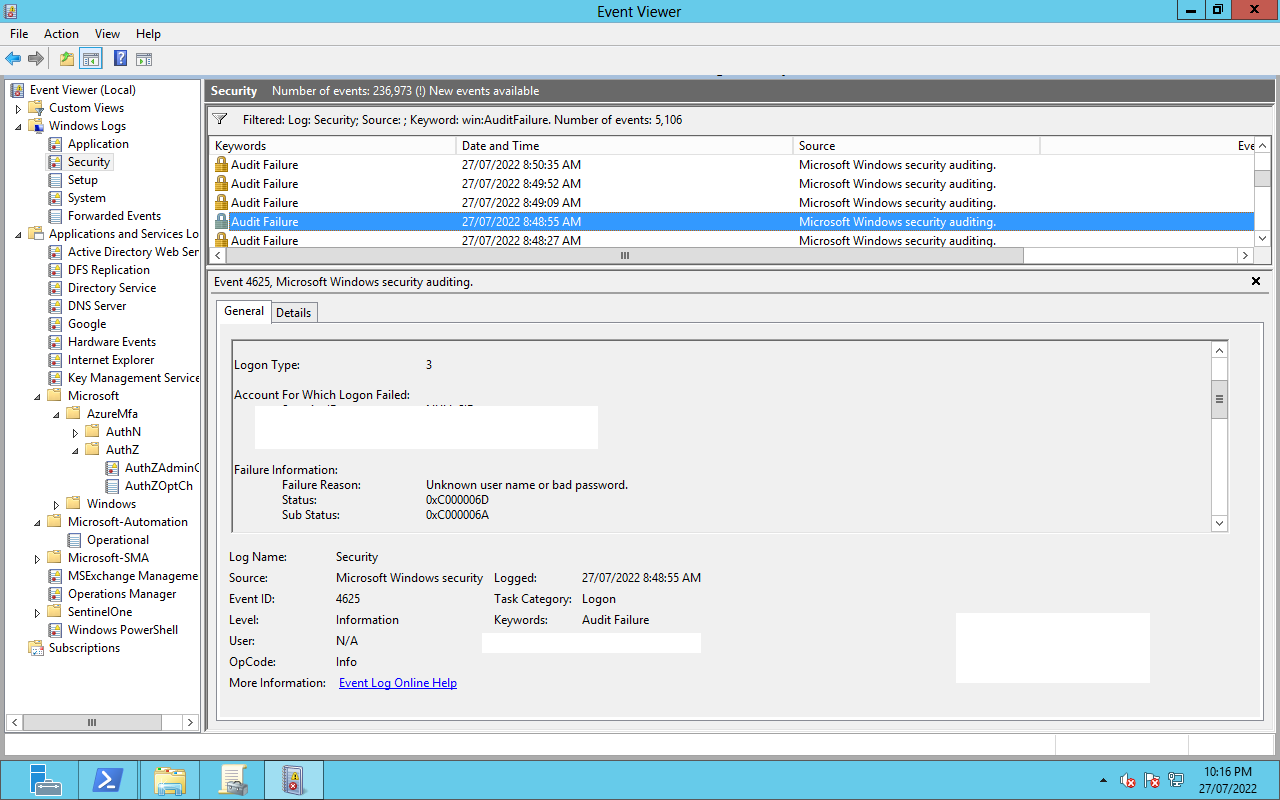
Event Viewer showed Unknown username or bad password in use.
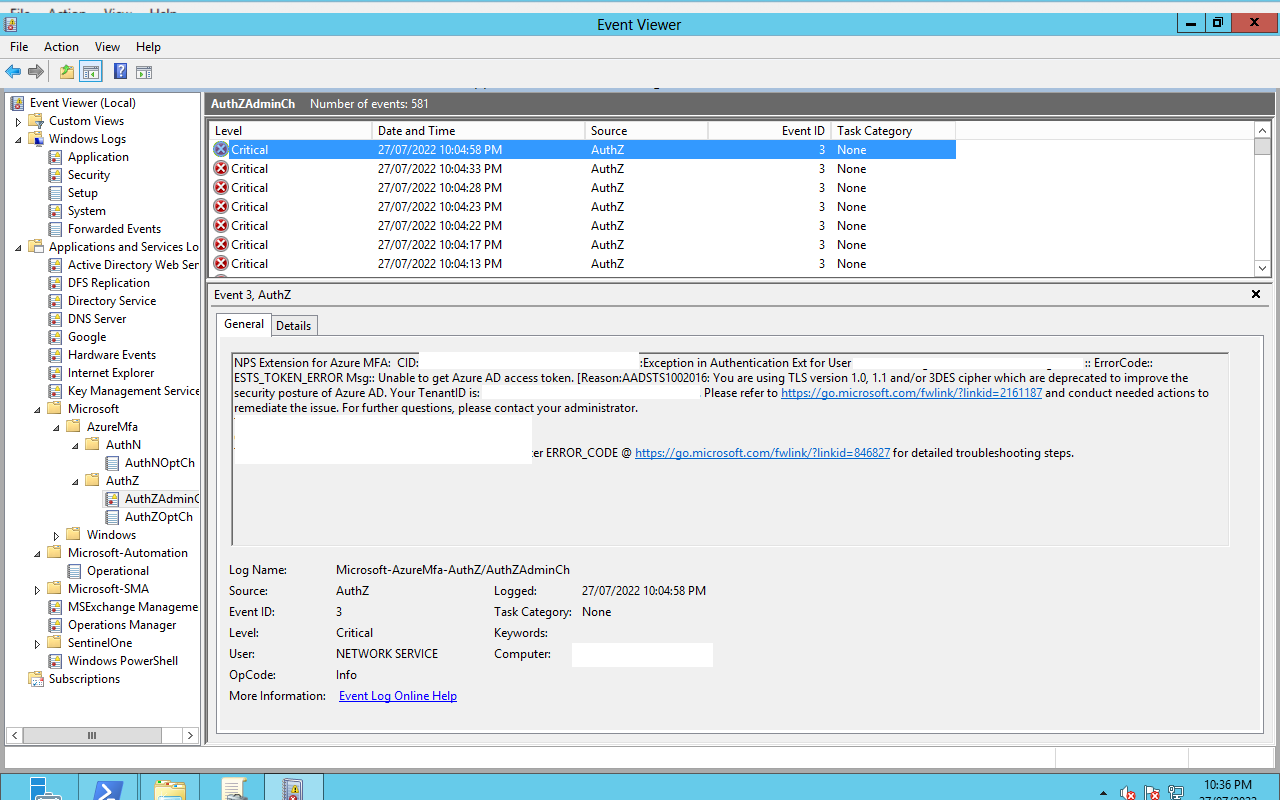
The NPS MFA extension leads you down a path that isn’t correct (for me). Dont trust this.
Also dont trust the reason codes in the NPS logs
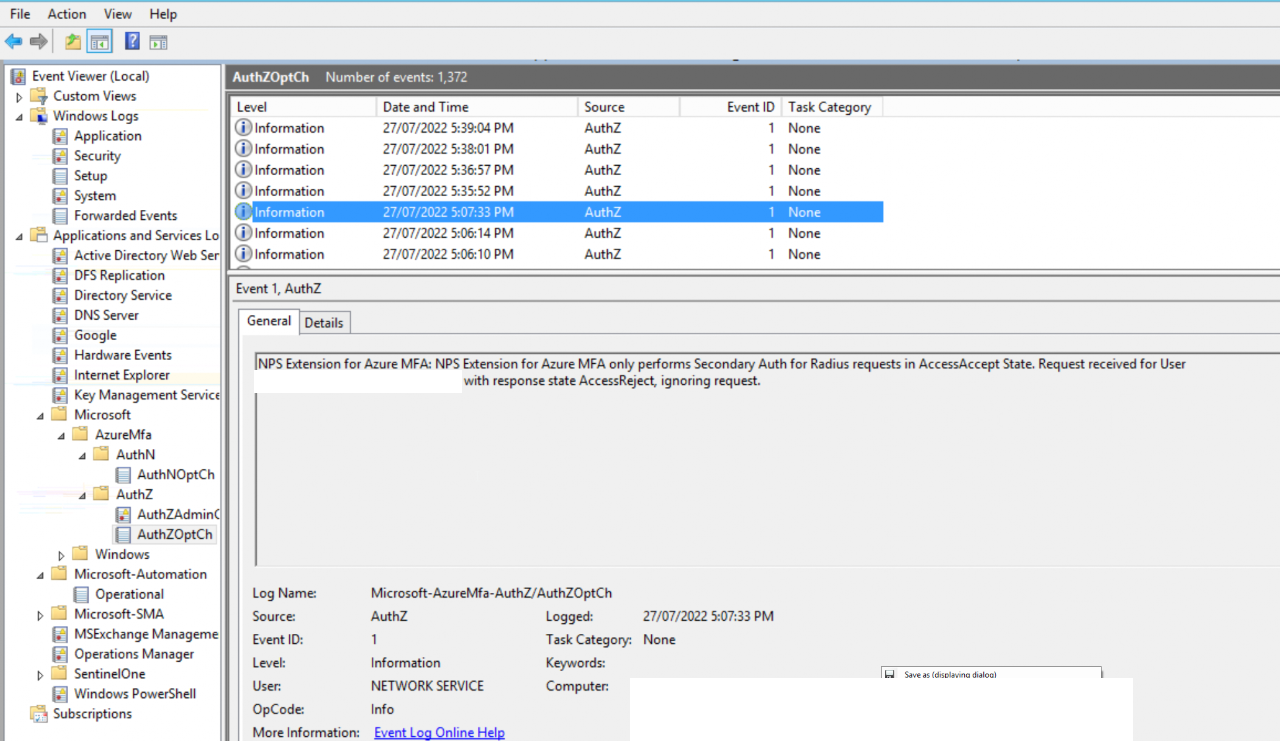
You may see reason code 21, <Reason-Code data_type=”0″>21</Reason-Code></Event> Further pointing to MFA extension issues.
To prove its not MFA related you can run the Check toolhttps://docs.microsoft.com/en-us/azure/active-directory/authentication/howto-mfa-nps-extension#:~:text=NPS%20extension%20health%20check%20script
Run with powershell and select option 1 to temporarily remove the MFA requirement and attempt a login to prove its not MFA.
New errors in NPS logs.
I was getting <Reason-Code data_type=”0″>16</Reason-Code> Not the most helpful and there are LOTS of results. But I found the below recent article which fixed it for me.
I did apply these keys for all the domain controllers. But that might be overkill and unnecessary. The real fix is to get off server 2012.
Note Certain fields, such as Issuer, Subject, and Serial Number, are reported in a “forward” format.You must reverse this format when you add the mapping string to the altSecurityIdentities attribute. For example, to add the X509IssuerSerialNumber mapping to a user, search the “Issuer” and “Serial Number” fields of the certificate that you want to map to the user. support.microsoft.com |
?
This isn’t complete yet, after enabling MFA I now have TLS and cipher errors from the MFA plugin.
But hopefully this will be an easy fix.