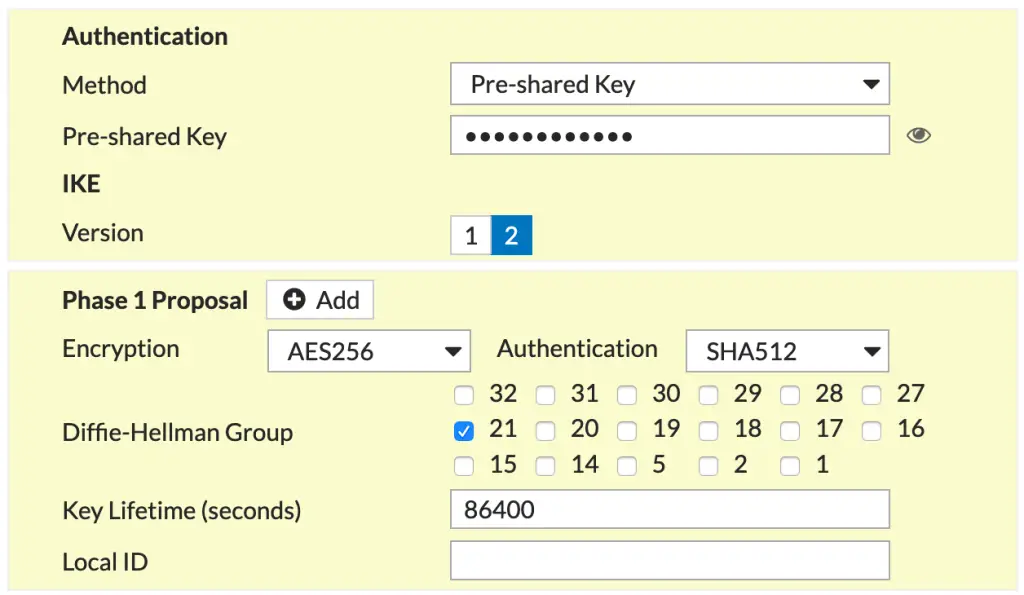
- Add VPN profile to both sides with same PreShared Key
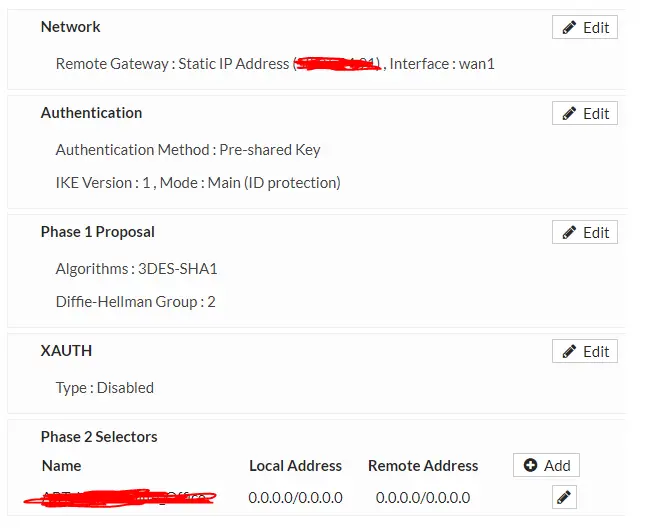
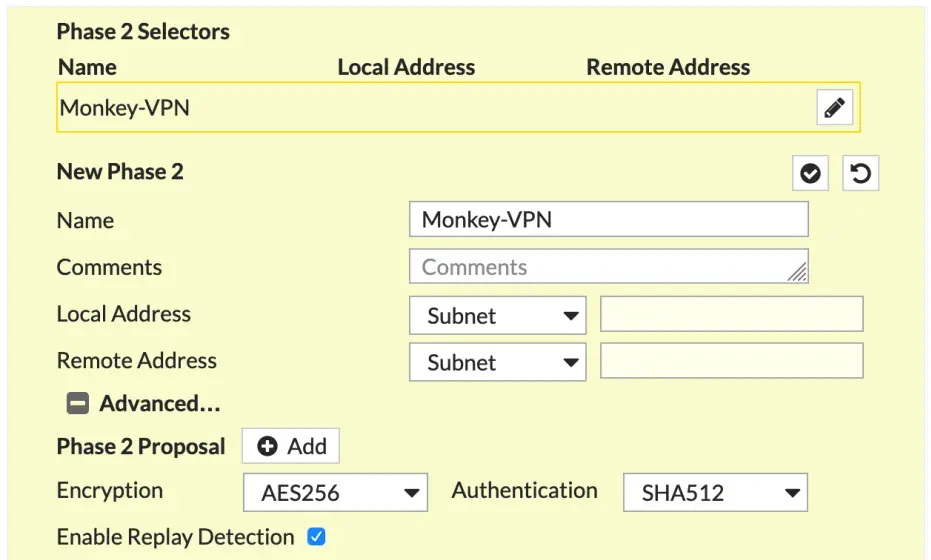
USE PFS for Phase 2 Auto Neg
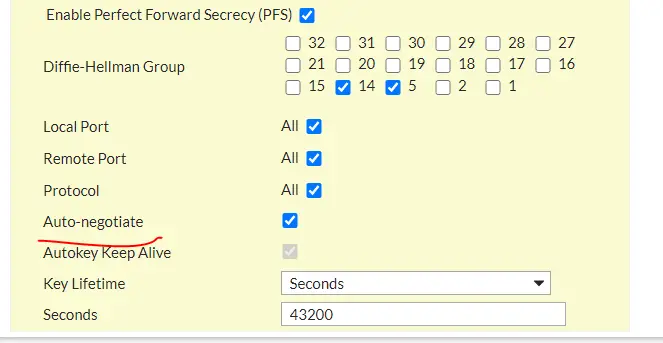
2) Add Static Routes on both sides to each other’s Subnets via the VPN Connection Interface created in Step 1
3) Add Policies
WAN->VPN Connection Interface created in Step 1 ( without NAT )
VPN Connection Interface created in Step 1 -> All ( without NAT )
***********
DES and 3DES does not need as strong a DH group, however DES and 3DES should never be used unless you are under some encryption restriction based on country restriction. AES should use a stronger DH Group. If you are using encryption or authentication algorithms with a 128-bit key, use Diffie-Hellman groups 19, 20. If you are using encryption or authentication algorithms with a 256-bit key or higher, use Diffie-Hellman group 21. RFC 5114 Sec 4 states DH Group 24 strength is about equal to a modular key that is 2048-bits long, that is not strong enough to protect 128 or 256-bit AES, you should stay away
