Recently setup a Site to Site ( S2S ) Connection into a VNET of an Azure Tenant
By Default the existing Network security group attached to the VNET allows VirtualNetwork Traffic ( Any <-> Any )
Virtual Network Gateway is Include in this Virtual Network Traffic
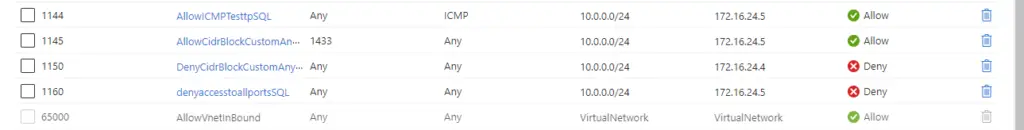
I needed to Limit the Inbound Ports allowed across this Gateway
As there is no NAT performed , I can target the Subnet or Subnets of the source Connection ( in this case 10.0.0.0/24) and enable 2 Deny rules for the two servers in the Vnet
I then created two allow rules above it for the traffic needed to Pass.
You can replicate the same setup for Outbound