There is a method to check whether a recently patched (or unknown) server is vulnerable to the SSRF exploit.
Please run this procedure for each of your assigned clients, either that have been or not patched, we MUST ensure they are not vulnerable, even if we think we applied the patch.
- Jump on a util machine inside customer network, or whatever machine as long as it is internal.
- Download nmap from nmap website and install with default settings
- Download nse script from Microsoft https://github.com/microsoft/CSS-Exchange/releases/latest/download/http-vuln-cve2021-26855.nse
- Move nse script file just download under c:\program files (386)\nmap\scripts
- Open nmap
- In the Command filed type: nmap -sV -p 443 –script=http-vuln-cve2021-26855 -script-args vulns.showall IPOFTHEEXCHANGESERVER
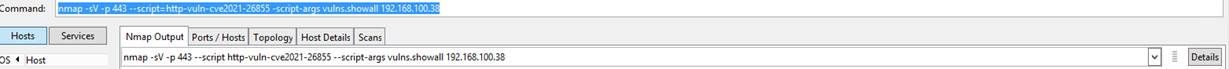
You must confirm it says “NOT VULNERABLE”
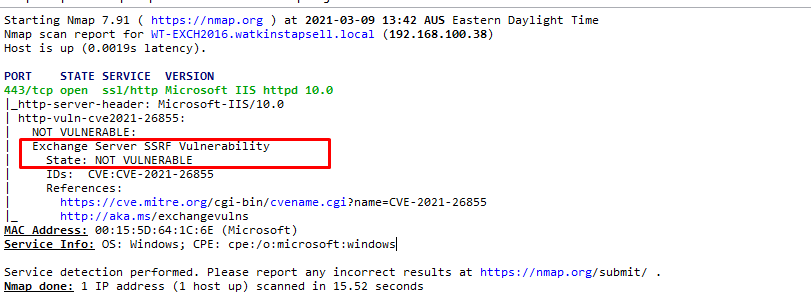
Example of vulnerable server:

What to do if your compromised
- Reset of all users’ account. ALL of them. Service accounts and administrator included.
- Review of all new users added/remove/edited during the last 2 weeks as well as security group change made.
- Immediate isolation of Exchange server (If server is exploited, full access is possible). Creation of a fresh Exchange, migrate mailboxes off the old Exchange (for this I invoke the Exchange experts). Burn the old Exchange server.
- Restore from Backup
- This repo contains all the hashes of the files you are supposed to have in Exchange. If something is different, consider the installation compromised. https://github.com/nccgroup/Cyber-Defence/tree/master/Intelligence/Exchange
- This repo has a ps1 script which will go through log/files to see whether there are indicator of compromise https://github.com/microsoft/CSS-Exchange/tree/main/Security
- This is provided by Microsoft https://docs.microsoft.com/en-us/windows/security/threat-protection/intelligence/safety-scanner-download

If you install the patch by downloading the patch and just double clicking on it, the patch will install but not fix the vulnerability because exchange services are still running, and it can’t replace the files.
See the known issues section. This also has a known side effect of leaving some services disabled.
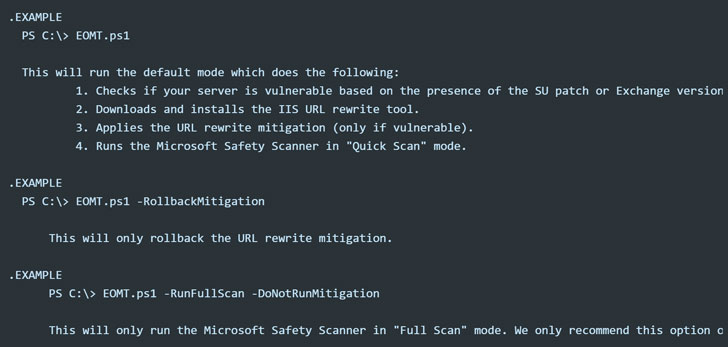
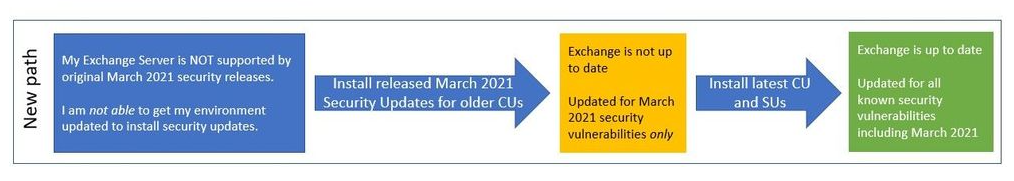
Microsoft released patches for older/unsupported Exchange CU’s to help customers securing their servers faster:

Microsoft on Monday released a one-click mitigation software that applies all the necessary countermeasures to secure vulnerable environments against the ongoing widespread ProxyLogon Exchange Server cyberattacks.
Called Exchange On-premises Mitigation Tool (EOMT), the PowerShell-based script serves to mitigate against current known attacks using CVE-2021-26855, scan the Exchange Server using the Microsoft Safety Scanner for any deployed web shells, and attempt to remediate the detected compromises.
“This new tool is designed as an interim mitigation for customers who are unfamiliar with the patch/update process or who have not yet applied the on-premises Exchange security update,” Microsoft said.
The development comes in the wake of indiscriminate attacks against unpatched Exchange Servers across the world by more than ten advanced persistent threat actors — most of the government-backed cyberespionage groups — to plant backdoors, coin miners, and ransomware, with the release of proof-of-concept (PoC) fueling the hacking spree even further.
Based on telemetry from RiskIQ, 317,269 out of 400,000 on-premises Exchange Servers globally have been patched as of March 12, with the U.S., Germany, Great Britain, France, and Italy leading the countries with vulnerable servers.
Additionally, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) has updated its guidance to detail as many as seven variants of the China Chopper web shell that are being leveraged by malicious actors.