The HTTPOnly attribute makes cookies inaccessible to JavaScript. Additionally, the Secure attribute
ensures that the cookie may only be transmitted over HTTPS. Cookies used by the application did
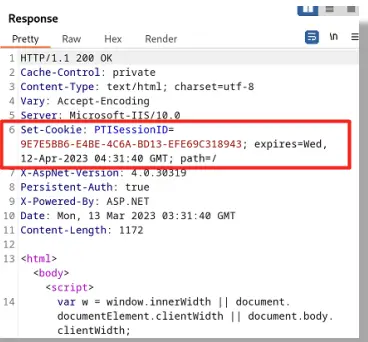
not have the HTTPOnly or Secure attribute set. This included but was not limited to the session
cookie PTISessionID.
Risk Rating – Medium (Likelihood: Unlikely; Impact: Moderate)
These cookies are accessible by client-side scripts and can be stolen in a cross-site scripting attack. In
the case of a session or user identification cookie, this can lead to account compromise
Enable Secure Flag in IIS
To enable secure flag in IIS, it is better to use URL Rewrite and add the following to your web.config file
<system.webServer>
<rewrite>
<outboundRules>
<rule name="Use only secure cookies" preCondition="Unsecured cookie">
<match serverVariable="RESPONSE_SET_COOKIE" pattern=".*" negate="false" />
<action type="Rewrite" value="{R:0}; secure" />
</rule>
<preConditions>
<preCondition name="Unsecured cookie">
<add input="{RESPONSE_SET_COOKIE}" pattern="." />
<add input="{RESPONSE_SET_COOKIE}" pattern="; secure" negate="true" />
</preCondition>
</preConditions>
</outboundRules>
</rewrite>
</system.webServer>Pre-Conditions wasn’t working on another site so I used this
<rewrite>
<outboundRules>
<rule name="Add HttpOnly">
<match serverVariable="RESPONSE_Set_Cookie" pattern=".+" />
<conditions>
<add input="{R:0}" pattern="; HttpOnly" negate="true" />
</conditions>
<action type="Rewrite" value="{R:0}; HttpOnly" />
</rule>
<rule name="Add Secure">
<match serverVariable="RESPONSE_Set_Cookie" pattern=".+" />
<conditions>
<add input="{R:0}" pattern="; Secure" negate="true" />
</conditions>
<action type="Rewrite" value="{R:0}; Secure" />
</rule>
</outboundRules>
</rewrite>