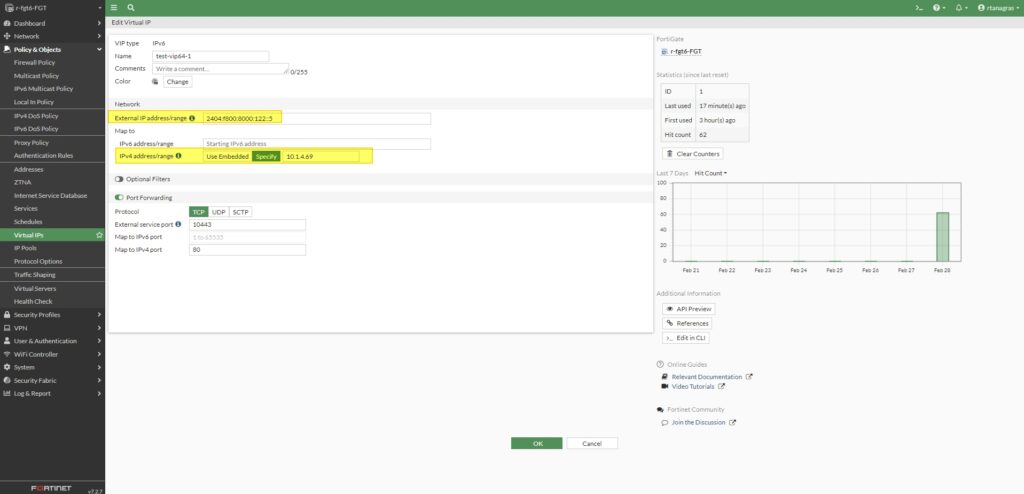
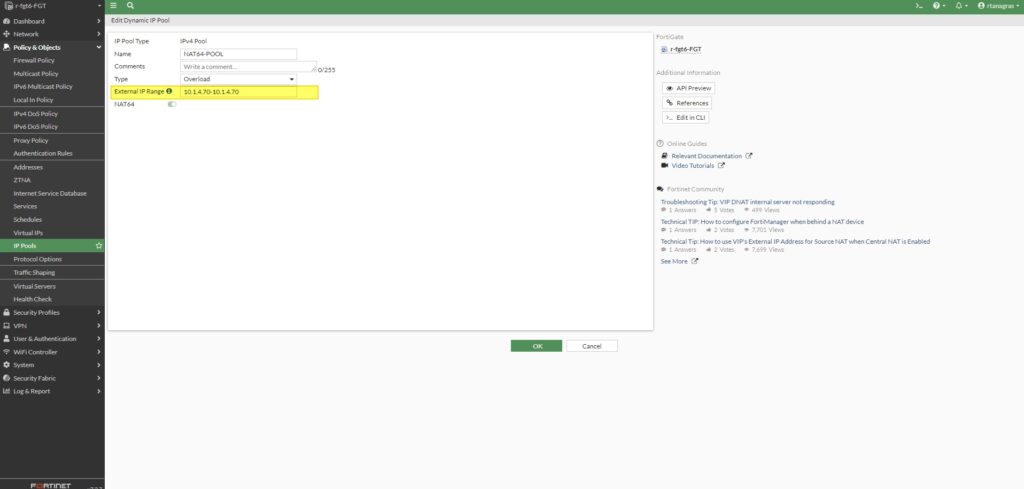
https://github.com/pariswells/public-code/blob/master/r-fgt6-FGT_7-2_1577_202402282151.conf
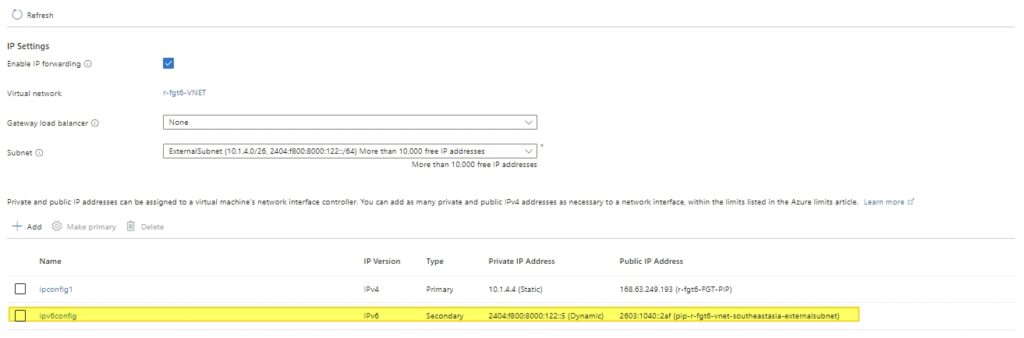
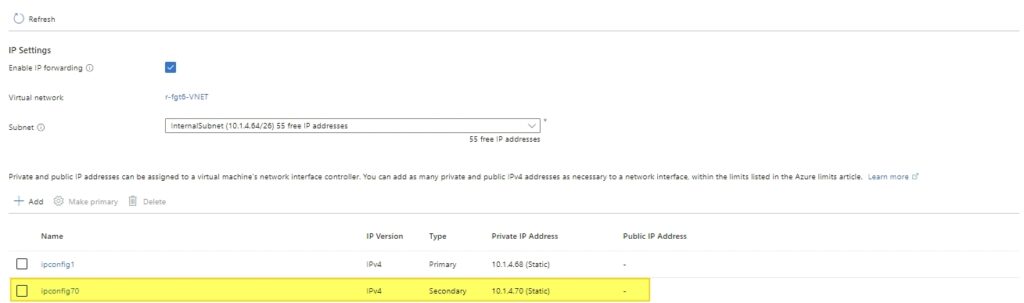
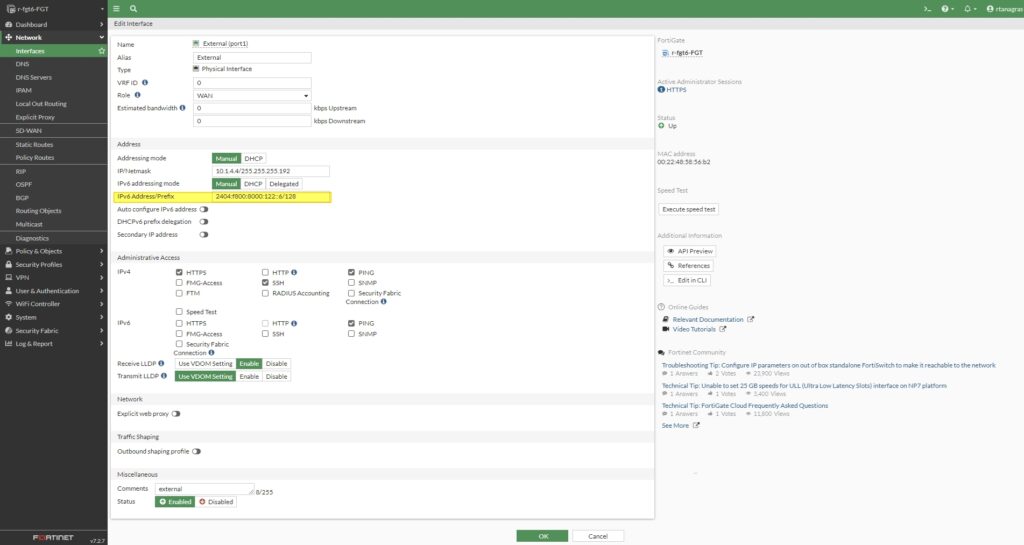
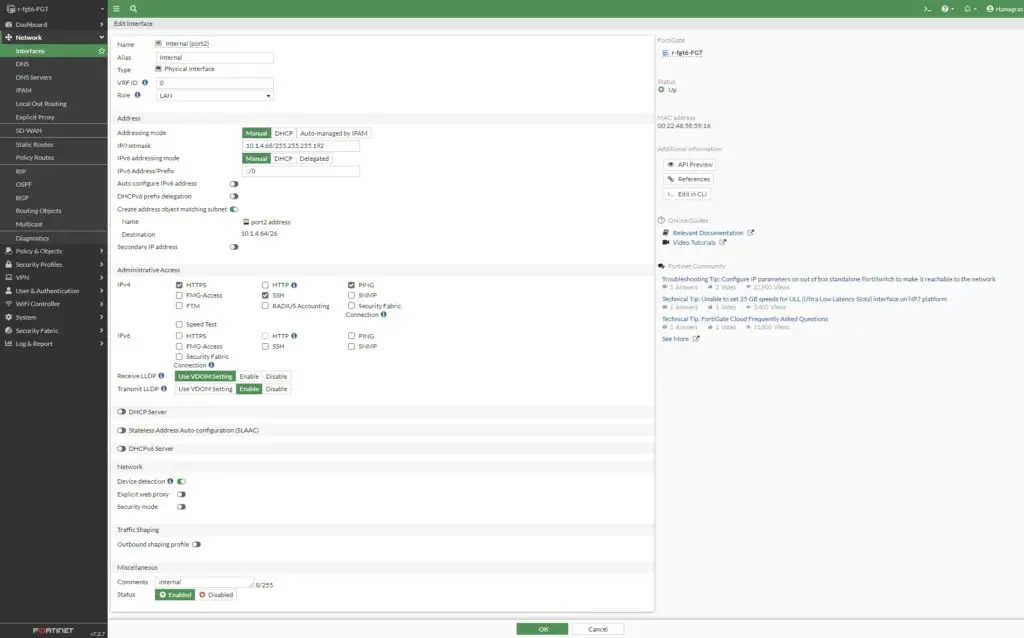
This does not work nicely , you have to add another IPv6 address to your NIC ( cannot just be one ) . One is for your external interface, and the other is for VIP. Additionally, on the internal NIC, you need to add another IPv4 address as a secondary IP in the internal interface, as we can’t use the IP address of your internal interface in the IP Pool.
The main issue is that on Azure, we can’t add multiple IPv6 addresses to a single interface. So, the workaround is to add a new NIC and attach it to your FortiGate. Then, we need to ensure that this NIC has an IPv6 address. Because we didn’t do this, your local traffic doesn’t know how to get out since the IP address is not set in the Azure NIC.