CIS -> ***https://www.cisecurity.org/benchmark/microsoft_365***
https://www.msb365.blog/?p=5832
GitHub – microsoft/zerotrustassessment: Repository for the Zero Trust Assessment project
Maester
Validate The Security Of Your Microsoft Cloud Environment With Maester – Sean McAvinue
Tenant Level Checking
- https://techcommunity.microsoft.com/t5/microsoft-entra-blog/public-preview-token-protection-for-sign-in-sessions/ba-p/3815756
- Check 2FA is enabled for all staff
- Set-OrganizationConfig -AutoEnableArchiveMailbox $true
- Windows Update Status -> Enable Windows Update for Business Reports (burgerhout.org)
- Retention Logs – https://pariswells.com/blog/research/365-audit-log-retention-everything-for-1-year/ ( Only Exchange \ AD \ Onedrive Sharepoint by default )
- https://blog.ciaops.com/2025/01/18/checking-your-environment-for-oversharing/
- BYOD Policy How to secure access on personal devices across your customers – (tminus365.com)
- Is https://config.office.com/ being users? OnedriveSync Health \ Update Policies
- Correct Licensing ( no extra licenses not applied )
- Conditional Access : https://tminus365.com/your-conditional-access-policies-suck/ – GitHub – aollivierre/ConditionalAccess: This repository contains a comprehensive set of Conditional Access (CA) policies and PowerShell management tools for Microsoft Entra ID (formerly Azure AD), designed to enhance your organization’s security posture while maintaining usability.
- Azure AD if used setup for Password Sync , make sure Passwords cannot be changed in 365 if they don’t have Azure AD p1
- Privileged Access Management in Microsoft 365 (admindroid.com) PAM
- What is Privileged Identity Management? – Microsoft Entra ID Governance | Microsoft Learn PIM
- Check Defender Endpoint Best Prac
- https://office365itpros.com/2021/03/11/external-email-tagging-exo/
- 365 has email Filtering Inbound and Outbound
- SPF should end with -all
- Break Glass Account – Best Practices for Break Glass Accounts – (tminus365.com)
- https://office365itpros.com/2021/07/20/block-self-service-purchases-of-windows-365-licenses/
- Branding Login Page to Stop Phising Attacks
- Outbound and Inbound Spam Policies should be enabled for Defender 365
- Safety Tips in Emails – Enable First Contact Safety Tip for Exchange Online (admindroid.com)
- DKIM Rotate keys at least every six months minimum of 2048-bit key
- DMARC Records ( Set to None if no reporting ) ( Vali for Dmarc )
- 365 Backup and Continuity ( Mimecast and Veeam )
- Technical Contact is correct and Notifications are set for service outage
- Global Litigation hold
- Check Mailbox auditing
- https://ourcloudnetwork.com/limit-local-administrators-on-microsoft-entra-joined-devices/
- Risky users
- Check Configuration analyzer https://security.microsoft.com/configurationAnalyzer
- E5 have they run the Attack simulation training?
- Set-OwaMailboxPolicy -Identity OwaMailboxPolicy-Default -AdditionalStorageProvidersAvailable $false
- Azure AD Logs 90 days ( E5 license for 1 Year )
- Retention Policy – Get-RetentionPolicy ( Make sure there’s a Tenant Retention Policy if the license admits one )
- Check No Retention Policy Hold ( Otherwise archive won’t work ) :Get-Mailbox -ResultSize unlimited | Where-Object {$_.RetentionHoldEnabled -eq $true} | Format-Table Name,RetentionPolicy,RetentionHoldEnabled -Auto 8.2)
- Deleted items retention – Get-Mailbox * | Where-Object {$_.Retaindeleteditemsfor -lt 30} | Format-Table name ( Increase Deleted Items from 14 days to 30 days)
- Run the Secure Score in O365 – https://securescore.microsoft.com/ ( https://support.office.com/en-us/article/how-to-check-office-365-service-health-932ad3ad-533c-418a-b938-6e44e8bc33b0 ? )
- Identity Secure Score as well
- Check modern auth is enabled on Exchange Online Get-OrganizationConfig | Format-Table Name,OAuth* -Auto
- Check and Report on any Email Forwarders -> https://gcits.com/knowledge-base/find-external-forwarding-mailboxes-office-365-customer-tenants-powershell/
- Check for any flow’s setup – You will need to create a flow in Microsoft Flow under the Domain account to search out flows and check them out – disabling any that forward email or alert a domain admin
- Check Oauth – Audit your Oath applications on the domain you didn’t have the first step locked down via: https://aad.portal.azure.com/#blade/Microsoft_AAD_IAM/StartboardApplicationsMenuBlade/AppAppsPreview this is as close as you can get to the M365 Microsoft Cloud App Security portal. and revoke anything that shouldn’t be there
Get-MsolCompanyInformation | Select DisplayName, UsersPermissionToUserConsentToAppEnabled - Enabled Zero-Hour Auto Purge for AntiSpam and Anti Malware
- Check Spam Policy ( https://docs.microsoft.com/en-us/microsoft-365/security/office-365-security/recommended-settings-for-eop-and-office365-atp?view=o365-worldwide )
- Image links to remote sites = OFF
- Numeric IP addresses = ON
- URL redirect to other port = ON
- URL to .biz or .info websites = ON
- Empty messages = ON
- Javascript or VBScript in HTML = ON
- Frame or iFrame tags in HTML = ON
- Object tags in HTML = ON
- Embed tags in HTML = ON
- Form tags in HTML = ON
- Web bugs in HTML = ON
- Apply sensitive word list = ON
- SPF record hard fail = ON
- Conditional sender ID hard fail = ON
- NDR backscatter = ON
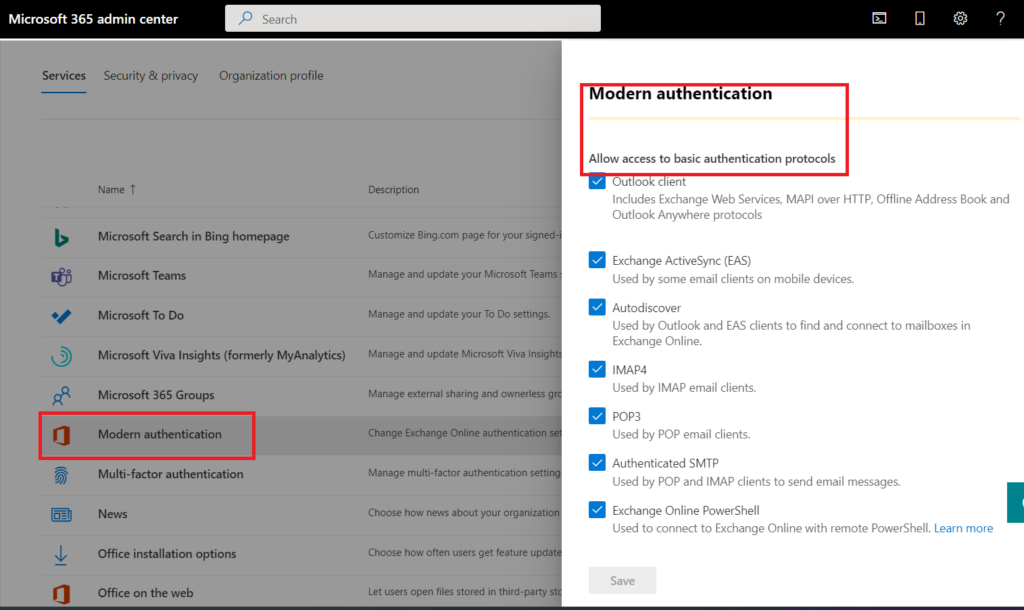
- Check to see if basic SMTP in O365 has been disabled – Disable SMTP Authentication in Exchange Online! – Joey Verlinden
- Check Conditional Access for Other Basic Auth ( Does not cover SMTP )
- Make sure there is a onmicrosoft.com administrator account documented incase anything wrong with adconnect sync
- Teams : Microsoft Teams Security Best Practices (admindroid.com) or https://tminus365.com/how-to-secure-microsoft-teams-top-tips/
- https://www.reddit.com/r/Office365/comments/18yjljh/cleanup_unused_azuread_enterprise_applications/
- Disable users being able to installed 3rd party Plugins : set-MsolCompanysettings -UsersPermissionToUserConsentToAppEnabled $false
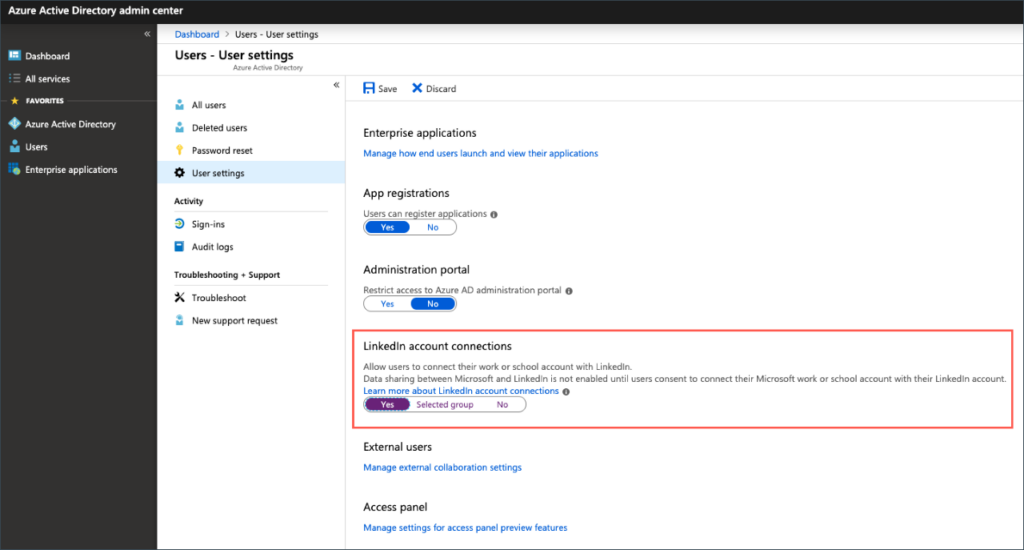
Default user role permissions
Users can register applications No
Restrict non-admin users from creating tenants Yes
Users can create security groups No
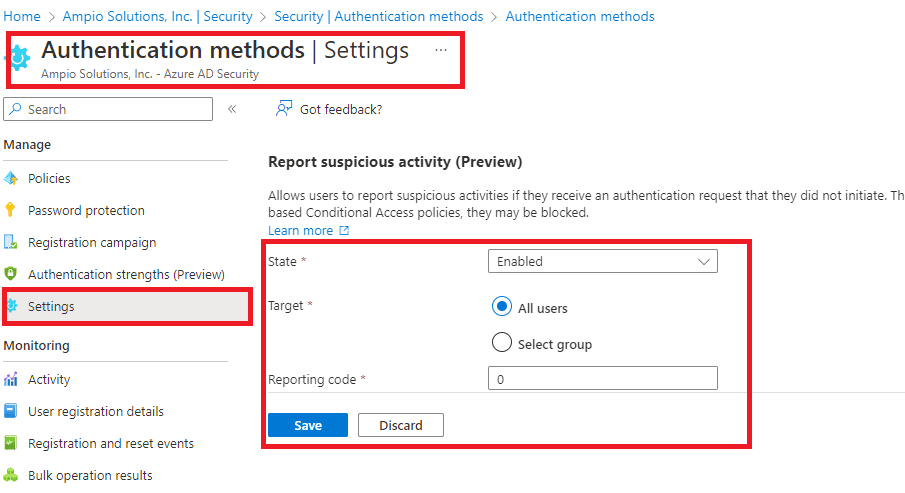
https://learn.microsoft.com/en-us/azure/active-directory/conditional-access/concept-continuous-access-evaluation?ocid=magicti_ta_learndoc Conditional Access Evaluation
Protect from MiTM Attacks? PasswordLess?
https://learn.microsoft.com/en-us/azure/active-directory/authentication/concept-system-preferred-multifactor-authentication
Show application name in push and passwordless notifications – Enabled
Show geographic location in push and passwordless notifications – Enabled
