Users who could connect were no longer connecting to our Foritgate
If using VDOM use
#conf Global
#diagnose sys top
Check for Free Memory Usage( Should not be over 80% )
Enable Debug for VPN
#dia debug en
#dia debug reset
#dia debug application sslvpn -1
Then Connect VPN , and check for logs for that user
Found :
“no more addresses” fortigate
#diagnose debug disable
#exec vpn sslvpn list
If using VDOM Use this before
#conf vdom
#edit Vdom Name
Users where getting 4 Address in the SSL VPN Sessions instead of one which was filling up the DHCP List
#fnsysctl ps
find the PID of sslvpnd
#run diag sys kill 11 <pid>
VPN Service will restart Automatically.
If FortiClient fails as the following stages, the likely cause is as follows:
10% – Local Network/PC issue
40% – Application or the Fortigate causing the error, occasionally caused by the local machines/network setup
45% – MultiFactor Authentication
80% – Username/Password issue
98% – corruption of services/often resolved by reinstalling the client on the laptop.
Client Logging
You will want to:
- Clear the logs if you have any there.
- Set the
Log LeveltoDebugto ensure the highest verbosity. (Make sure to disabled after troubleshooting) - Run the attempt, and then
Export logs
Client: Access Sydney
Device: Fortigate 60E
FortiOS ver 6.4.3
Symptoms:
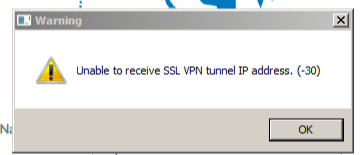
- User connects to VPN but Forticlient errors, Unable to receive SSL VPN tunnel IP address -30
- Checked the Fortigate, no VPN users connected
- 20 free IP address in the VPN IP Pool
Troubleshooting:
- Enabled debugging, reattempted connection and found error relating to IP allocation failure
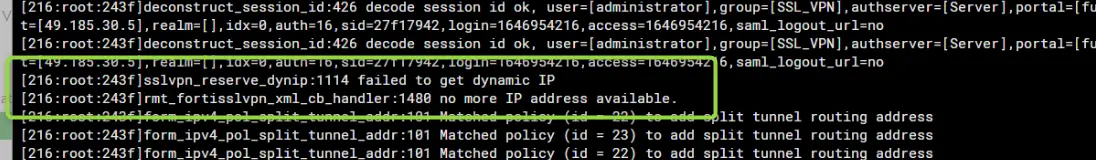
Quick fix: killed the sslvpnd process (this will terminate all VPN connections)
Found that a later version of FortiOS has fixed this bug: