Useful email to send out to users to stop them click on Crypto Links
Hello,
There is a virus doing the rounds called CryptoLocker currently . More can be found – https://en.wikipedia.org/wiki/CryptoLocker
Putting it briefly, this virus is downloaded onto a computer usually by a fake email attachment or through a website popup. Once downloaded and run by accident , it starts encrypting all the company data on shared drives automatically and once completed will Ransom the data with an undisclosed amount to be paid anonymously. The only way to restore from this will be a restore from the backups the night before.
Please be vigilant with any emails you open from third parties you are not expecting and more importantly Message Attachments opened, below are some example of Email Message Spoofs’
—–Original Message—–
From: John Doe [mailto:[email protected]]
Sent: Tuesday, October 15, 2013 10:34 AM
To: Jane Doe
Subject: Annual Form – Authorization to Use Privately Owned Vehicle on State Business
All employees need to have on file this form STD 261 (attached). The original is retained by supervisor and copy goes to Accounting. Accounting need this form to approve mileage reimbursement.
The form can be used for multiple years, however it needs to re-signed annually by employee and supervisor.
Please confirm all employees that may travel using their private car on state business (including training) has a current STD 261 on file. Not having a current copy of this form on file in Accounting may delay a travel reimbursement claim.
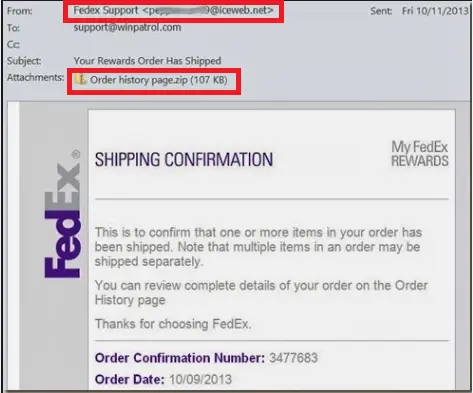
Auspost
Each computer became infected after opening an EMAIL from AUSTRALIA POST (or AUSPOST), with a subject line such as:
Subject: An agent was unable to redeem the parcel to your place for the reason: receiver was absent
There have been many different subject lines but they commonly want you to click on an attachment or a link such as “Down Load Shipping Label”
More info here: http://auspost.com.au/about-us/scam-email-warning.html
TNT Courier
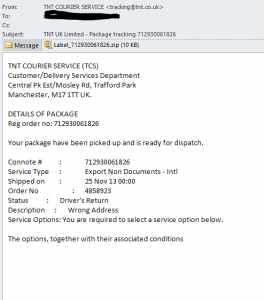
Australian Federal Police
Sample email:
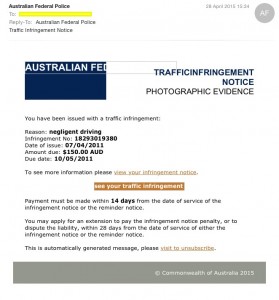
————————————————————– Another
CryptoLocker is a ransomware trojan which targeted computers running Microsoft Windows. CryptoLocker propagated via infected email attachments, usually in Scripts (filename.bat), Word (filename.doc / .docx), Excel (filename.xls / .xlsx), Zip (filename.zip / .rar) or Executable files (filename.exe).
CryptoLocker encrypts files across local hard drives and mapped network drives. The process encrypts data files with certain extensions, including Microsoft Office, OpenDocument, and other documents, pictures, and database files. These files are then locked up and render inaccessible. Once it has done enough damage you will get a pop-up message similar to below:
Although CryptoLocker itself is readily removed, files remained encrypted in a way which many considered unfeasible to break. Many said that the ransom should not be paid, but did not offer any way to recover files; others said that paying the ransom was the only way to recover files that had not been backed up. Some victims claimed that paying the ransom did not always lead to the files being decrypted.
Since CryptoLocker has many version and has been evolving till date. It has been known to infect PCs even with up-to-date antivirus due to a term called “Zero-day malware” which means a brand new variant that is not discovered by security companies.
“A zero–day virus (also known as zero–day malware or next-generation malware) is a previously unknown computer virus or other malware for which specific antivirus software signatures are not yet available. Traditionally, antivirus software relies upon signatures to identify malware.”
However, we can avoid getting caught from such infection as most of them comes in the following email form:
- Infringement notice
- Court Cases
- Water / Electricity Bills
- Parcel collection from AusPost and other popular courier services
- Banking services such as Paypal and even legitimate banks (Commbank, Westpac & etc.)
Below is an example Email which may contain CryptoLocker infection. This email does not come with any attachment however it has a few hyperlinks which is tempting users to click on in order to execute an attack from external source. Please pay attention to the red boxes for tips:
- Always check the sender name, in many cases they are completely random however there are chances that it may come from yourself (a.k.a email spoofing) or someone you know. You should be well aware that your colleague would not be such representative in sending you such emails.
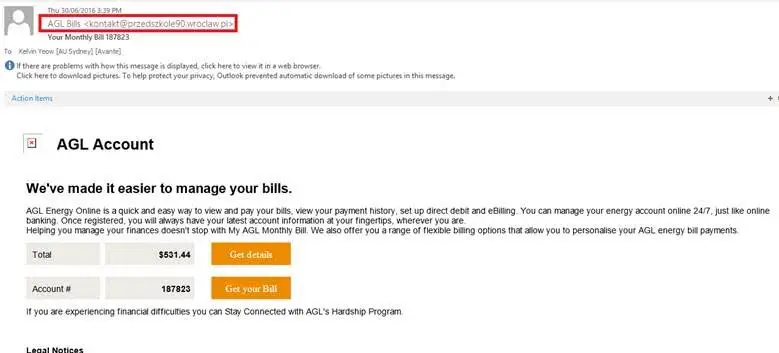
- Then next tip is without clicking on the links simply hover your mouse and Outlook should automatically show you the link you’re about to visit. It will pop-out with an address as per below red box. A legit link from agl should have something more common like agl.com.au. In some cases they can even create a fake link over what seems like a legit link like below example:
This is an example fake hyperlink created which actually goes to a completely different site. For this experiment I have embeded https://www.google.com.au on a https://www.agl.com.au text.
I hope you find this informative and please pass on the message to everyone to help keep our network a safer environment.
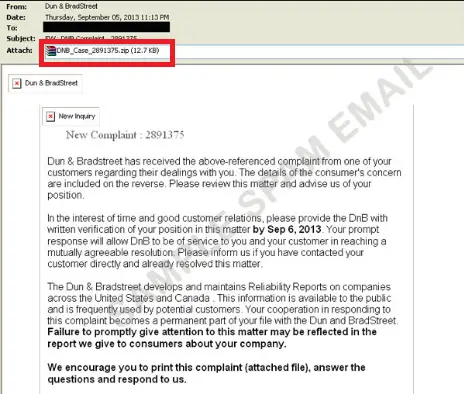
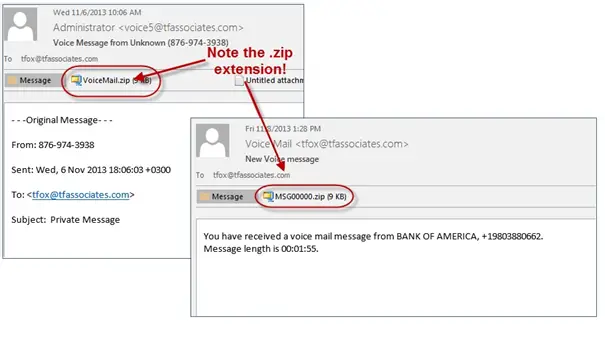
Below are a few more example emails and variations that disguised as potential CryptoLocker infection.