Compatibility of 3g/4G usb modems can be found here :
http://cookbook.fortinet.com/configuring-modems-fortigate/#List_of_the_Current_Supported_LTE_Modems
Always a time when an ISP doesn’t deliver internet to premises so the office is without Internet. Thanks to 4g connections , you can pipe internet out through that however most VPN’s need static IP’s which you don’t get with 4g / 3g cards. Fortinet provides a DDNS service for this problem per : http://video.fortinet.com/video/99/site-to-site-ipsec-vpn-setup-with-dynamic-interface , however some providers assign IP’s on their private network ( Telstra ) so you need to put the VPN in aggressive mode and authenticate with Passkey
here is the config to get the VPN working on a Fortinet Firewall.
See here how to get the Modem working : //pariswells.com/blog/fixes/fortinet-60d-model-with-telstra-sierra-wireless-320u
**** MAKE SURE YOU HAVE ROUTE and POLICY SET or the Interface won’t come up
Remote Office VPN Config
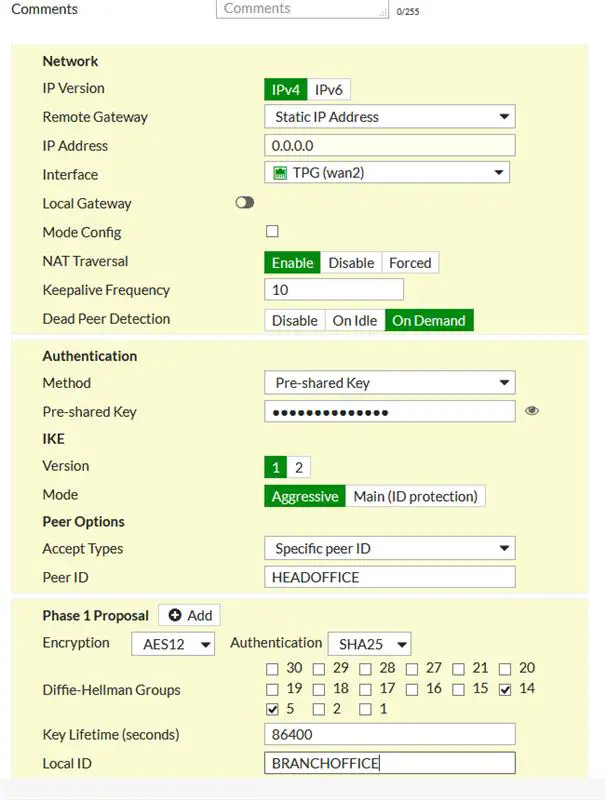
config vpn ipsec phase1
edit "VPN"
set interface "modem"
set dhgrp 2
set proposal aes128-sha1
set remote-gw **IP-Address of remote-gw**
set psksecret ENC ***PASSKEY***
next
end
config vpn ipsec phase2
edit "192.168.10.0-192.168.11.0"
set phase1name "VPN"
set proposal aes128-sha1
set keepalive enable
set dhgrp 2
set keylifeseconds 3600
set src-subnet 192.168.16.0 255.255.255.0
set dst-subnet 192.168.18.0 255.255.255.0
next
end
Remote Office Firewall Config
config firewall policy
edit 8
set srcintf "wan1"
set dstintf "modem"
set srcaddr "192.168.16.0/24"
set dstaddr "192.168.18.0/24"
set action ipsec
set schedule "always"
set service "ALL"
set logtraffic all
set inbound enable
set outbound enable
set vpntunnel "VPN"
next
edit 4
set srcintf "wan1"
set dstintf "modem"
set srcaddr "all"
set dstaddr "all"
set action accept
set schedule "always"
set service "ALL"
set logtraffic all
set nat enable
next
edit 5
set srcintf "switch"
set dstintf "modem"
set srcaddr "all"
set dstaddr "all"
set action accept
set schedule "always"
set service "ALL"
set logtraffic all
set nat enable
next
edit 6
set srcintf "switch"
set dstintf "wan1"
set srcaddr "all"
set dstaddr "all"
set action accept
set schedule "always"
set service "ALL"
next
edit 7
set srcintf "wan1"
set dstintf "switch"
set srcaddr "all"
set dstaddr "all"
set action accept
set schedule "always"
set service "ALL"
next
end
Main Office
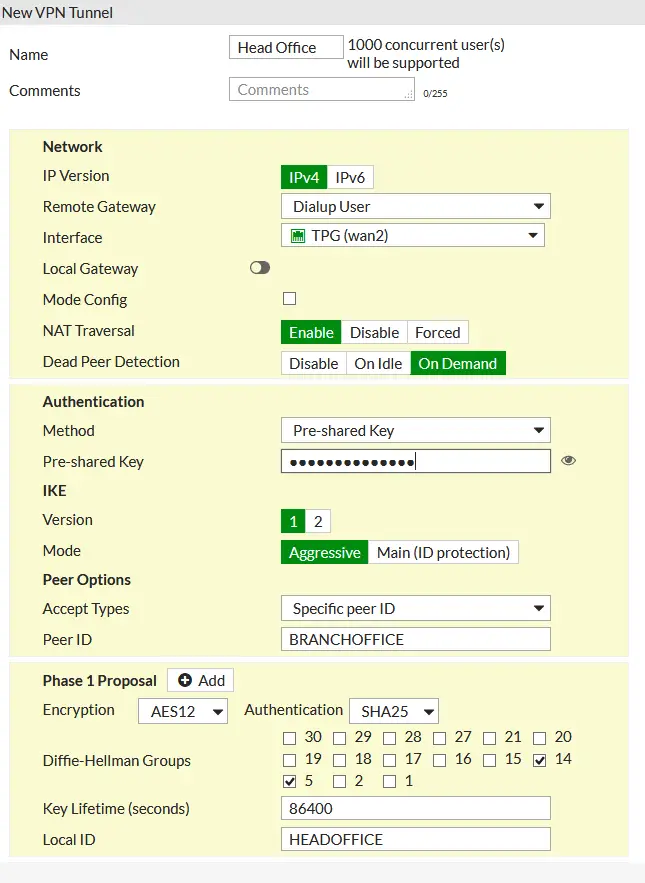
edit "VPN"
set vdom "root"
set type tunnel
set snmp-index 25
set interface "*INTERNET**"
nex
edit "VPN"
set type dynamic
set interface "*INTERNET**"
set keylife 28800
set proposal aes128-sha1
set comments "VPN"
set dhgrp 2
set psksecret ENC **passphrase**
next
edit "192.168.16.0-192.168.18.0"
set phase1name "VPN"
set proposal aes128-sha1
set dhgrp 14 2
set keepalive enable
set keylifeseconds 3600
set src-subnet 192.168.18.0 255.255.255.0
set dst-subnet 192.168.16.0 255.255.255.0
next


